-
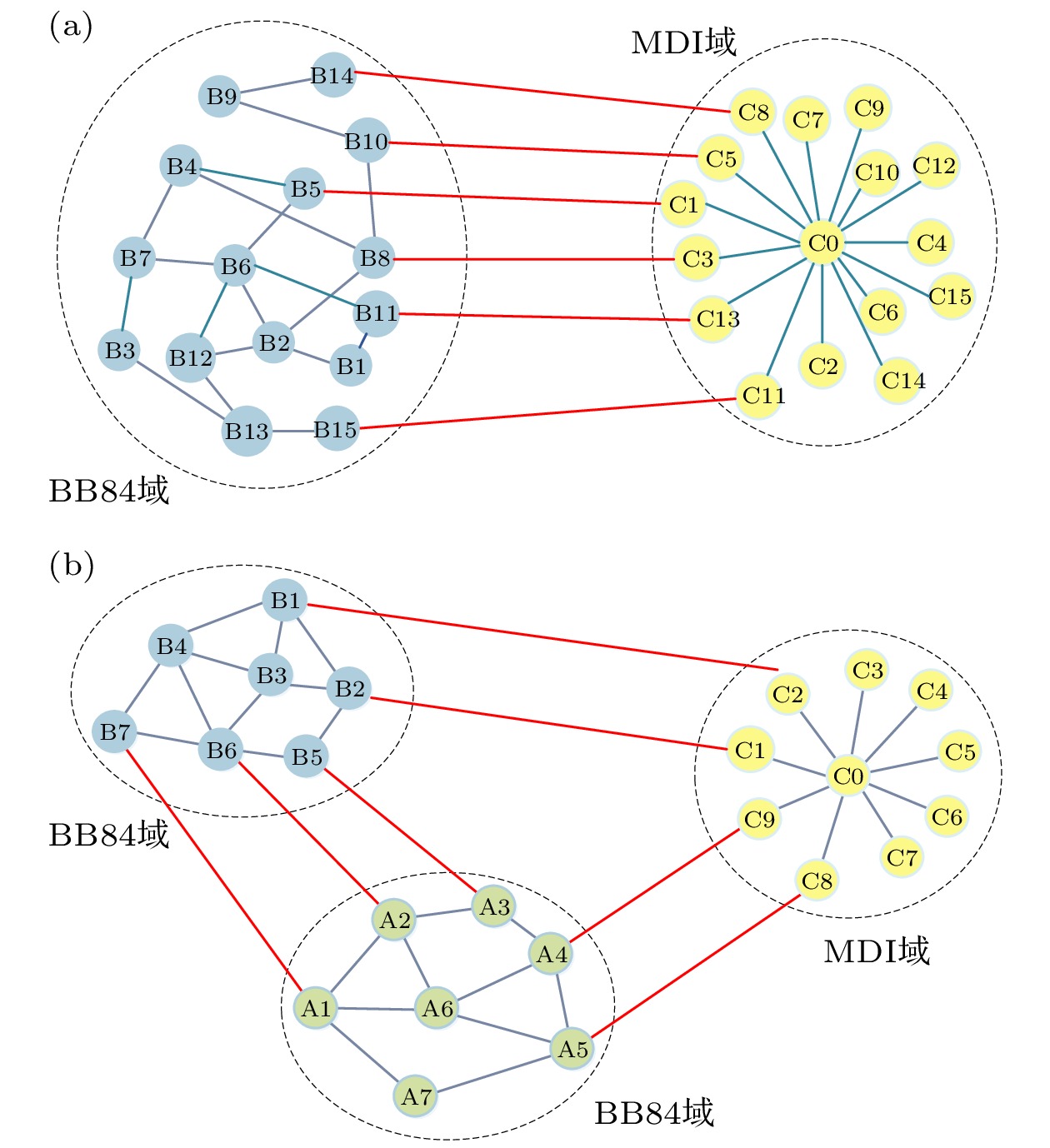
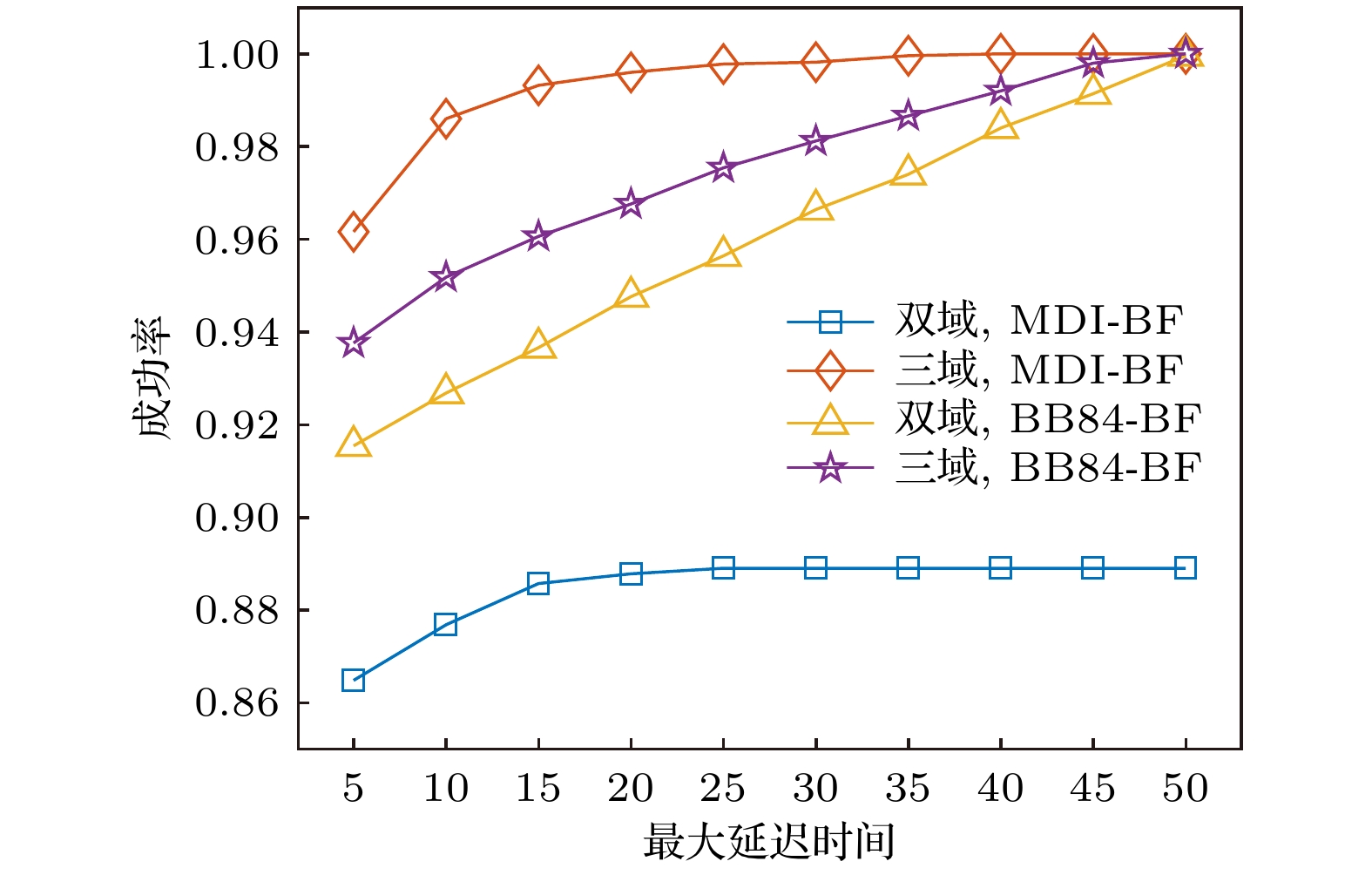
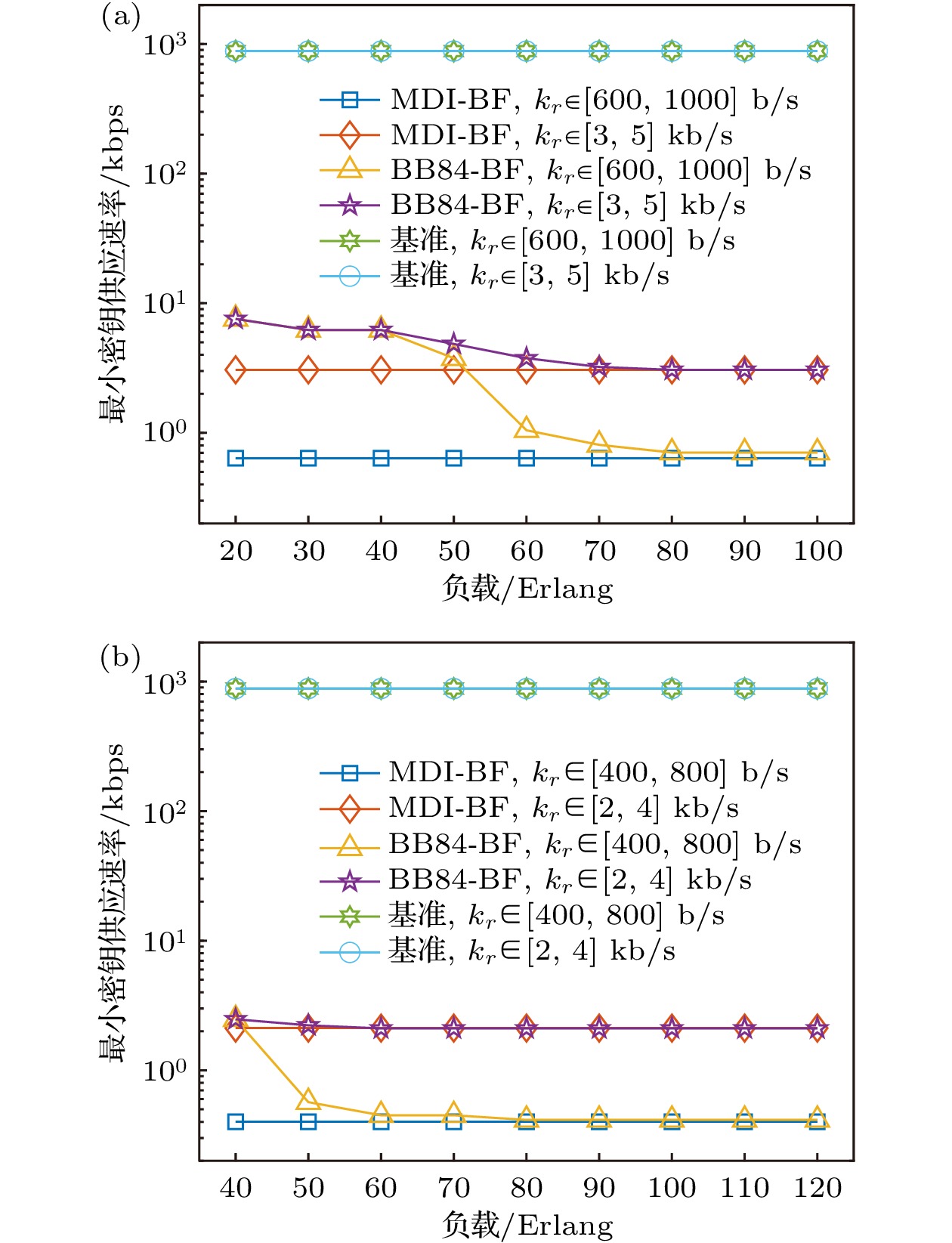
Most of the existing metropolitan quantum networks are implemented based on a single quantum key distribution protocol, and interconnecting metropolitan quantum networks implemented by different protocols are the development trend of large-scale quantum networks, but there are still some problems in the provision of inter-domain key services, such as low possibility of success and mismatch between key supply and demand. To solve the above problems, this paper proposes two on-demand inter-domain key service provisioning strategies for multi-domain cross-protocol quantum networks, namely, on-demand provisioning strategy based on BB84 bypass first (BB84-BF) and on-demand provisioning strategy based on MDI bypass first (MDI-BF). Meanwhile, a service provisioning model for multi-domain cross-protocol quantum networks is constructed, and an on-demand inter-domain key service provisioning algorithm is designed. Moreover, numerical simulations and performance evaluation are carried out under two scenarios: high key rate demand and low key rate demand for two-domain and three-domain quantum network topologies. Simulation results verify that the proposed on-demand provisioning strategies have better applicability to different multi-domain quantum networks. In addition, for different key rate requirements, the MDI-BF strategy and BB84-BF strategys have different performance advantages under different performance indicators. For example, in terms of the success possibility of inter-domain key service requests, the MDI-BF strategy is more suitable for the low key rate requirements (~30% higher than the traditional strategies in two domain topologies), while the BB84-BF strategy is more suitable for the high key rate requirements (~19% higher than the traditional strategies under two domain topologies). In addition, compared with the traditional strategies, the proposed on-demand provisioning strategies can increase the balance degree between key supply and demand by more than one order of magnitude. Hence, the proposed strategies can reduce the cost of inter-domain key service provisioning and improve the realistic security level.
-
Keywords:
- multi-domain quantum networks /
- quantum key distribution /
- cross-protocol /
- key service provisioning
[1] Yang Z, Zolanvari M, Jain R 2023 IEEE Commun. Surveys Tuts. 25 1059
 Google Scholar
Google Scholar
[2] Gill S S, Kumar A, Singh H, Singh M, Kaur K, Usman M, Buyya R 2022 Softw. Pract. Exp. 52 66
 Google Scholar
Google Scholar
[3] Lo H K, Curty M, Tamaki K 2014 Nat. Photon. 8 595
 Google Scholar
Google Scholar
[4] Pirandola S, Andersen U L, Banchi L, Berta M, Bunandar D, Colbeck R, Englund D, Gehring T, Lupo C, Ottaviani C, Pereira J L, Razavi M, Shamsul S J, Tomamichel M, Usenko V C, Vallone G, Villoresi P, Wallden P 2020 Adv. Opt. Photon. 12 1012
 Google Scholar
Google Scholar
[5] Bennett C H, Brassard G 1984 IEEE Int. Conf. Comput. Syst. Signal Process. Bangalore, India, January, 1984 p175
[6] Lo H K, Curty M, Qi B 2012 Phys. Rev. Lett. 108 130503
 Google Scholar
Google Scholar
[7] Li W, Zhang L K, Tan H, Lu Y C, Liao S K, Huang J, Li H, Wang Z, Mao H K, Yan B Z, Li Q, Liu Y, Zhang Q, Peng C Z, You L X, Xu F H, Pan J W 2023 Nat. Photon. 17 416
 Google Scholar
Google Scholar
[8] Yin H L, Fu Y, Li C L, Weng C X, Li B H, Gu J, Lu Y S, Huang S, Chen Z B 2023 Nat. Sci. Rev. 10 nwac228
 Google Scholar
Google Scholar
[9] Cao Y, Zhao Y, Wang Q, Zhang J, Ng S X, Hanzo L 2022 IEEE Commun. Surveys Tuts. 24 839
 Google Scholar
Google Scholar
[10] Tang Y L, Yin H L, Zhao Q, Liu H, Sun X X, Huang M Q, Zhang W J, Chen S J, Zhang L, You L X, Wang Z, Liu Yang, Lu C Y, Jiang X, Ma X F, Zhang Q, Chen T Y, Pan J W 2016 Phys. Rev. X 6 011024
 Google Scholar
Google Scholar
[11] Joshi S K, Aktas D, Wengerowsky S, Lončarić M, Neumann S P, Liu B, Scheidl T, Lorenzo G C, Samec Ž, Kling L, Qiu A, Razavi M, Stipčević M, Rarity J G, Ursin R 2020 Sci. Adv. 6 eaba0959
 Google Scholar
Google Scholar
[12] Avesani M, Foletto G, Padovan M, Calderaro L, Agnesi C, Bazzani E, Berra F, Bertapelle T, Picciariello F, Santagiustina F, Scalcon D, Scriminich A, Stanco A, Vedovato F, Vallone G, Villoresi P 2023 Quantum Computing, Communication, and Simulation III San Francisco, United States, 2023 p112
[13] Cao Y, Zhao Y L, Zhang J, Wang Q, Niyato D, Hanzo L 2022 IEEE Netw. 36 14
 Google Scholar
Google Scholar
[14] Cao Y, Zhao Y L, Zhang J, Wang Q 2022 IEEE Commun. Mag. 60 38
 Google Scholar
Google Scholar
[15] Zhou L, Lin J P, Xie Y M, Lu Y S, Jing Y M, Yin H L, Yuan Z L 2023 Phys. Rev. Lett. 130 250801
 Google Scholar
Google Scholar
[16] Fan-Yuan G J, Lu F Y, Wang S, Yin Z Q, He D Y, Zhou Z, Teng J, Chen W, Guo G C, Han Z F 2021 Photonics Res. 9 1881
 Google Scholar
Google Scholar
[17] Tysowski P K, Ling X, Lütkenhaus N, Mosca M 2018 Quantum Sci. Technol. 3 024001
 Google Scholar
Google Scholar
[18] Li P, Yu X, Zhao Y, Zhang J 2023 Opto-Electronic and Communications Conference Shanghai, China, July 2–6, 2023 p1
[19] Gottesman D, Lo H K, Lutkenhaus N, Preskill J 2004 Quantum Inf. Comput. 4 325
 Google Scholar
Google Scholar
[20] Ma X F, Qi B, Zhao Y, Lo H K 2005 Phys. Rev. A 72 012326
 Google Scholar
Google Scholar
[21] Xu F H, Xu H, Lo H K 2014 Phys. Rev. A 89 052333
 Google Scholar
Google Scholar
[22] Ma X F, Fung C H F, Razavi M 2012 Phys. Rev. A 86 052305
 Google Scholar
Google Scholar
[23] Wang X B 2013 Phys. Rev. A 87 012320
 Google Scholar
Google Scholar
[24] Yu Z W, Zhou Y H, Wang X B 2013 Phys. Rev. A 88 062339
 Google Scholar
Google Scholar
[25] Curty M, Xu F, Cui W, Lim C C W, Tamaki K, Lo H K 2014 Nat. Commun. 5 3732
 Google Scholar
Google Scholar
[26] Wang Q, Wang X B 2014 Sci. Rep. 4 4612
 Google Scholar
Google Scholar
[27] Zhou Y H, Yu Z W, Wang X B 2016 Phys. Rev. A 93 042324
 Google Scholar
Google Scholar
-
表 1 域间密钥业务按需提供算法
Table 1. Algorithm for on-demand provisioning of inter-domain key services.
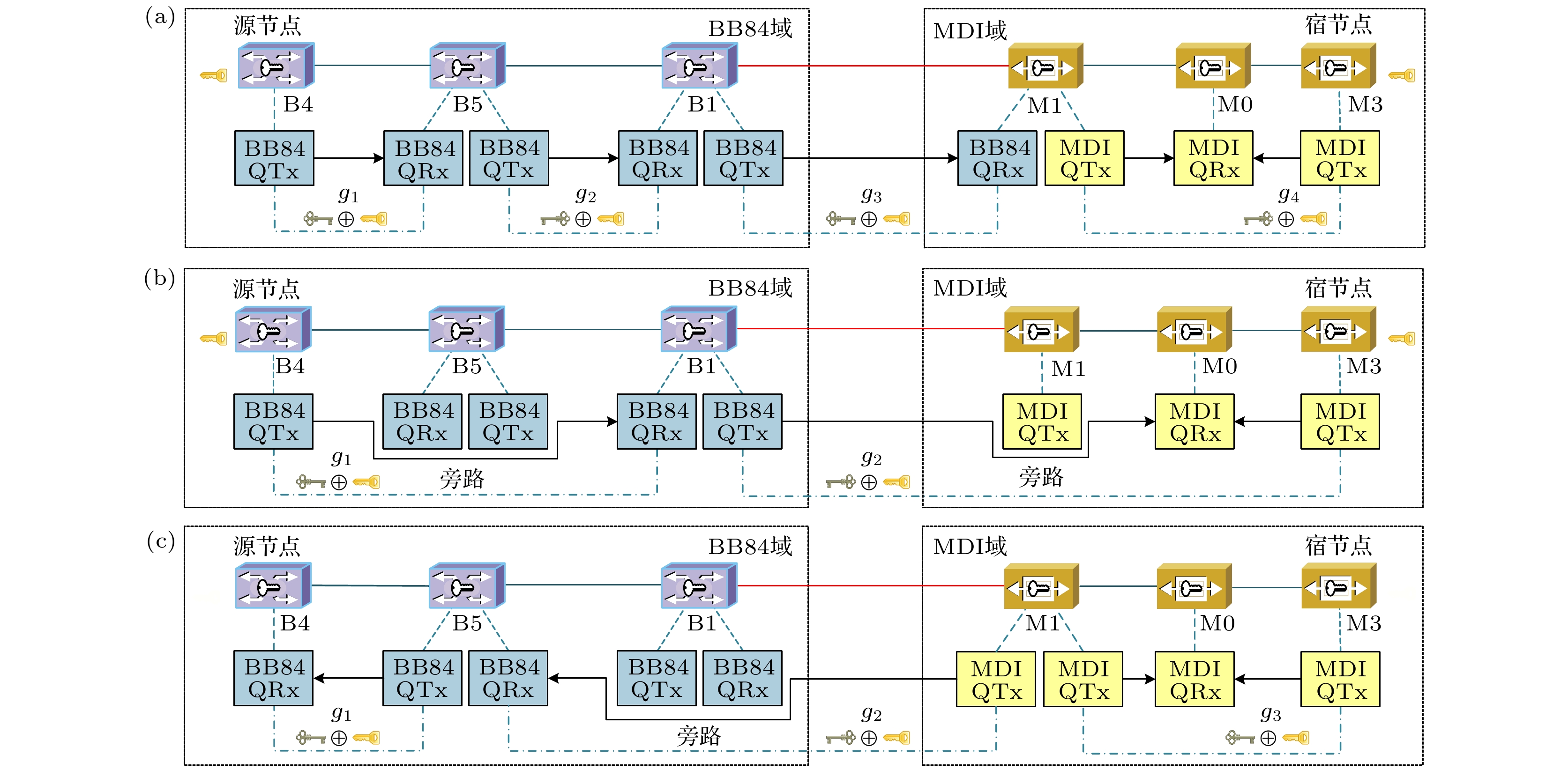
输入: $G\left( {V, E} \right)$, ${V_{\text{B}}}$, ${V_{\text{M}}}$, ${V_{{\text{BJ}}}}$, ${V_{{\text{MJ}}}}$, $R$ 输出: 每个成功的域间密钥业务的密钥中继路径${p_r}\left( {{N_{{p_r}}}, {L_{{p_r}}}, {B_{{p_r}}}, {m_{{p_r}}}} \right)$, ${R_{\text{S}}}$ 1 初始化变量${R_{\text{S}}} \leftarrow \emptyset $; 2 for 每个域间密钥业务请求$r\left( {{s_r}, {d_r}, {k_r}, {t_r}} \right) \in R$ do 3 更新全网各节点设备占用状态; 4 如果源宿节点没有可用的QKD设备, 则该业务失败; 5 if 执行BB84-BF策略 then 6 for ${v_i} \in {V_{{\text{MJ}}}}$ do 7 if ${\lambda _{{v_i}}} < 2$ then 8 将${v_i}$从$V$中移除并更新$E$; 9 end if 10 end for 11 end if 12 基于K短路径算法计算源宿节点间的K条备选密钥中继路径, 路径集合为${P_r}$; 13 if ${P_r} = \emptyset $ then 14 域间密钥业务请求r失败; 15 end if 16 for 每条密钥中继路径${p_r}\left( {{N_{{p_r}}}, {L_{{p_r}}}, {B_{{p_r}}}, {m_{{p_r}}}} \right) \in {P_r}$ do 17 ${N_{{p_r}}} \leftarrow $${p_r}$经过的QKD节点集合, ${L_{{p_r}}} \leftarrow $${p_r}$经过的QKD链路集合, ${B_{{p_r}}} \leftarrow \emptyset $, ${m_{{p_r}}} \leftarrow {p_r}$的密钥供应
速率;18 for $n_{{p_r}}^i \in {N_{{p_r}}}$ do 19 if 执行MDI-BF策略 && $n_{{p_r}}^i \in {V_{{\text{MJ}}}}$ then 20 ${B_{{p_r}}} \leftarrow \{ {B_{{p_r}}}, n_{{p_r}}^i\} $; 21 end if 22 if $n_{{p_r}}^i \in {V_{\text{B}}}$ && $n_{{p_r}}^i \ne {d_r}$ && $n_{{p_r}}^i \ne {s_r}$ && (${\lambda _{n_{{p_r}}^i}} = 0~||~{\varepsilon _{n_{{p_r}}^i}} = 0 $) then 23 ${B_{{p_r}}} \leftarrow \{ {B_{{p_r}}}, n_{{p_r}}^i\} $; 24 end if 25 end for 26 ${m_{{p_r}}} \leftarrow $根据更新后的密钥中继路径重新计算${m_{{p_r}}}$; 27 if ${m_{{p_r}}} < {k_r}$ then 28 continue; 29 else 30 for $n_{{p_r}}^i \in {N_{{p_r}}}$do 31 if 旁路$n_{{p_r}}^i$后密钥中继路径密钥供应速率$ \geqslant {k_r}$ then 32 ${B_{{p_r}}} \leftarrow \{ {B_{{p_r}}}, n_{{p_r}}^i\} $, 更新${m_{{p_r}}}$; 33 end if 34 end for 35 将${p_r}$作为域间密钥业务r的最终密钥中继路径, ${R_{\text{S}}} \leftarrow \left\{ {{R_{\text{S}}}, r} \right\}$; 36 break; 37 end if 38 end for 39 如果${P_r}$中没有满足密钥率需求的密钥中继路径, 则该业务失败; 40 end for 41 return 每个成功的域间密钥业务的密钥中继路径${p_r}\left( {{N_{{p_r}}}, {L_{{p_r}}}, {B_{{p_r}}}, {m_{{p_r}}}} \right)$, ${R_{\text{S}}}$ 表 2 密钥生成率仿真参数
Table 2. Simulation parameters for key rates.
参数 取值 真空态误码率${e_0}$ 0.5 本底误码${e_{\text{d}}}$/% 1 暗计数率${p_{\text{d}}}$ ${10^{ - 7}}$ 探测效率${\eta _{\text{d}}}$/% 40 纠错效率${f_{\text{e}}}$ 1.16 光纤衰减常数$\alpha $/(dB·km–1) 0.2 重复频率/GHz 1 -
[1] Yang Z, Zolanvari M, Jain R 2023 IEEE Commun. Surveys Tuts. 25 1059
 Google Scholar
Google Scholar
[2] Gill S S, Kumar A, Singh H, Singh M, Kaur K, Usman M, Buyya R 2022 Softw. Pract. Exp. 52 66
 Google Scholar
Google Scholar
[3] Lo H K, Curty M, Tamaki K 2014 Nat. Photon. 8 595
 Google Scholar
Google Scholar
[4] Pirandola S, Andersen U L, Banchi L, Berta M, Bunandar D, Colbeck R, Englund D, Gehring T, Lupo C, Ottaviani C, Pereira J L, Razavi M, Shamsul S J, Tomamichel M, Usenko V C, Vallone G, Villoresi P, Wallden P 2020 Adv. Opt. Photon. 12 1012
 Google Scholar
Google Scholar
[5] Bennett C H, Brassard G 1984 IEEE Int. Conf. Comput. Syst. Signal Process. Bangalore, India, January, 1984 p175
[6] Lo H K, Curty M, Qi B 2012 Phys. Rev. Lett. 108 130503
 Google Scholar
Google Scholar
[7] Li W, Zhang L K, Tan H, Lu Y C, Liao S K, Huang J, Li H, Wang Z, Mao H K, Yan B Z, Li Q, Liu Y, Zhang Q, Peng C Z, You L X, Xu F H, Pan J W 2023 Nat. Photon. 17 416
 Google Scholar
Google Scholar
[8] Yin H L, Fu Y, Li C L, Weng C X, Li B H, Gu J, Lu Y S, Huang S, Chen Z B 2023 Nat. Sci. Rev. 10 nwac228
 Google Scholar
Google Scholar
[9] Cao Y, Zhao Y, Wang Q, Zhang J, Ng S X, Hanzo L 2022 IEEE Commun. Surveys Tuts. 24 839
 Google Scholar
Google Scholar
[10] Tang Y L, Yin H L, Zhao Q, Liu H, Sun X X, Huang M Q, Zhang W J, Chen S J, Zhang L, You L X, Wang Z, Liu Yang, Lu C Y, Jiang X, Ma X F, Zhang Q, Chen T Y, Pan J W 2016 Phys. Rev. X 6 011024
 Google Scholar
Google Scholar
[11] Joshi S K, Aktas D, Wengerowsky S, Lončarić M, Neumann S P, Liu B, Scheidl T, Lorenzo G C, Samec Ž, Kling L, Qiu A, Razavi M, Stipčević M, Rarity J G, Ursin R 2020 Sci. Adv. 6 eaba0959
 Google Scholar
Google Scholar
[12] Avesani M, Foletto G, Padovan M, Calderaro L, Agnesi C, Bazzani E, Berra F, Bertapelle T, Picciariello F, Santagiustina F, Scalcon D, Scriminich A, Stanco A, Vedovato F, Vallone G, Villoresi P 2023 Quantum Computing, Communication, and Simulation III San Francisco, United States, 2023 p112
[13] Cao Y, Zhao Y L, Zhang J, Wang Q, Niyato D, Hanzo L 2022 IEEE Netw. 36 14
 Google Scholar
Google Scholar
[14] Cao Y, Zhao Y L, Zhang J, Wang Q 2022 IEEE Commun. Mag. 60 38
 Google Scholar
Google Scholar
[15] Zhou L, Lin J P, Xie Y M, Lu Y S, Jing Y M, Yin H L, Yuan Z L 2023 Phys. Rev. Lett. 130 250801
 Google Scholar
Google Scholar
[16] Fan-Yuan G J, Lu F Y, Wang S, Yin Z Q, He D Y, Zhou Z, Teng J, Chen W, Guo G C, Han Z F 2021 Photonics Res. 9 1881
 Google Scholar
Google Scholar
[17] Tysowski P K, Ling X, Lütkenhaus N, Mosca M 2018 Quantum Sci. Technol. 3 024001
 Google Scholar
Google Scholar
[18] Li P, Yu X, Zhao Y, Zhang J 2023 Opto-Electronic and Communications Conference Shanghai, China, July 2–6, 2023 p1
[19] Gottesman D, Lo H K, Lutkenhaus N, Preskill J 2004 Quantum Inf. Comput. 4 325
 Google Scholar
Google Scholar
[20] Ma X F, Qi B, Zhao Y, Lo H K 2005 Phys. Rev. A 72 012326
 Google Scholar
Google Scholar
[21] Xu F H, Xu H, Lo H K 2014 Phys. Rev. A 89 052333
 Google Scholar
Google Scholar
[22] Ma X F, Fung C H F, Razavi M 2012 Phys. Rev. A 86 052305
 Google Scholar
Google Scholar
[23] Wang X B 2013 Phys. Rev. A 87 012320
 Google Scholar
Google Scholar
[24] Yu Z W, Zhou Y H, Wang X B 2013 Phys. Rev. A 88 062339
 Google Scholar
Google Scholar
[25] Curty M, Xu F, Cui W, Lim C C W, Tamaki K, Lo H K 2014 Nat. Commun. 5 3732
 Google Scholar
Google Scholar
[26] Wang Q, Wang X B 2014 Sci. Rep. 4 4612
 Google Scholar
Google Scholar
[27] Zhou Y H, Yu Z W, Wang X B 2016 Phys. Rev. A 93 042324
 Google Scholar
Google Scholar
Catalog
Metrics
- Abstract views: 3918
- PDF Downloads: 94
- Cited By: 0















 DownLoad:
DownLoad: