-
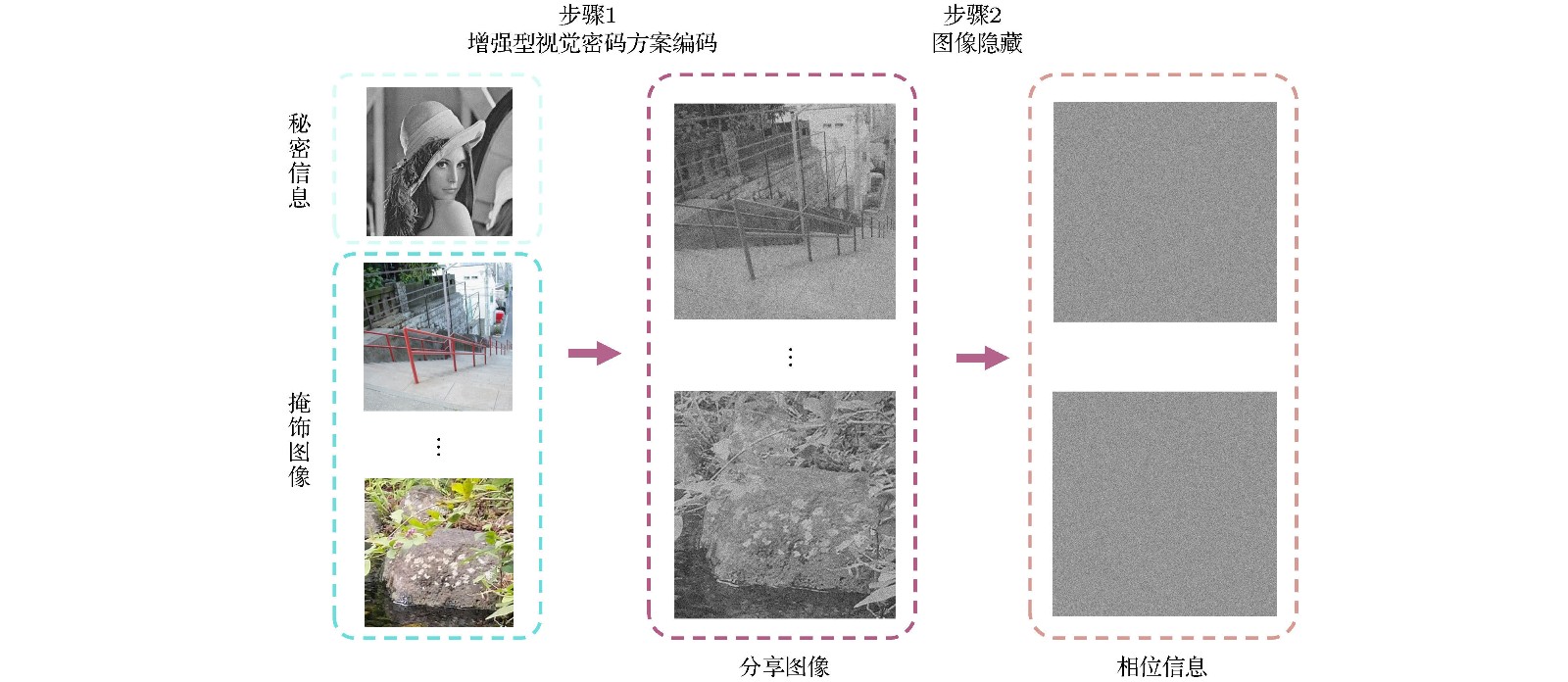
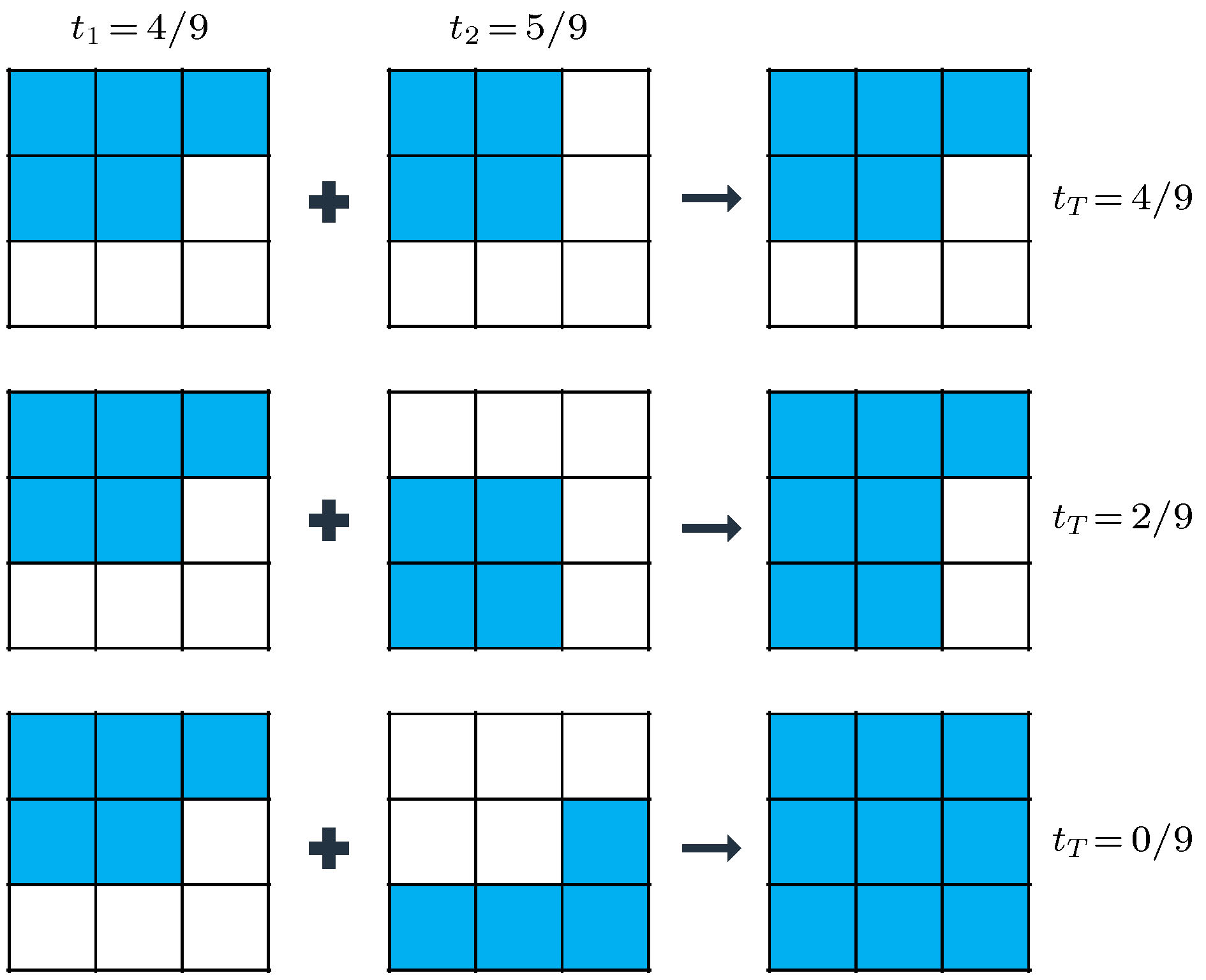
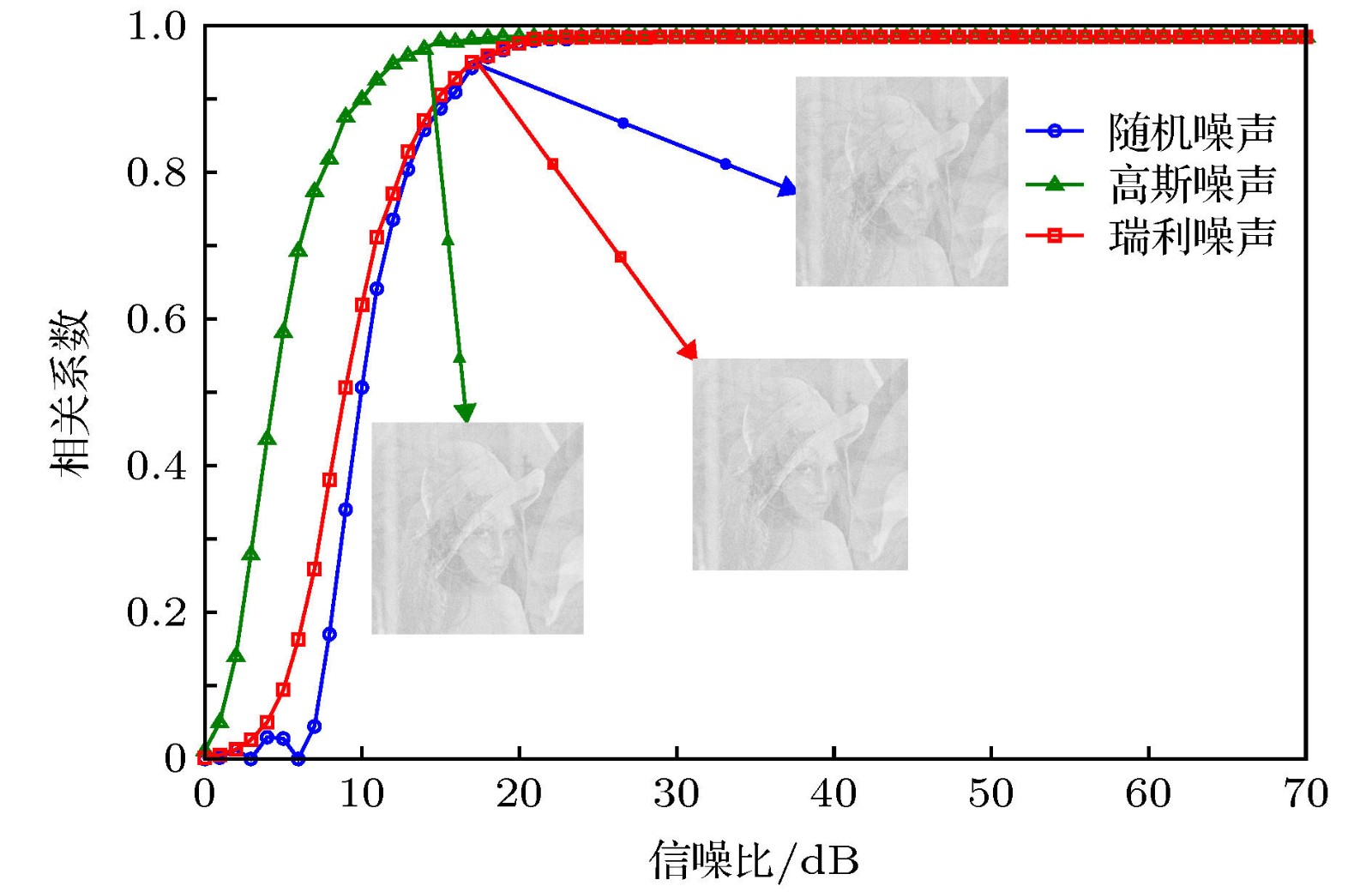
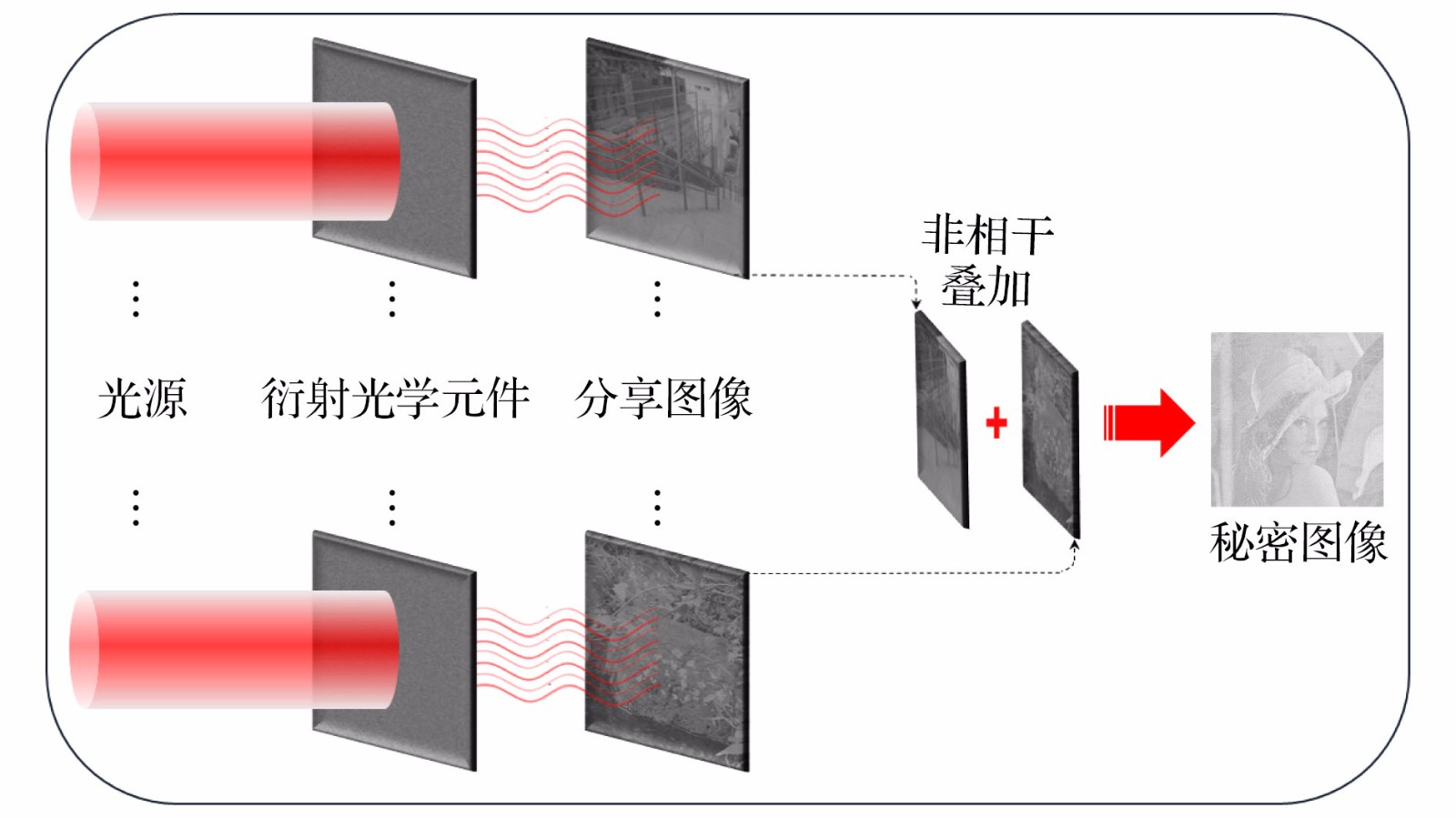
Recent years, with the rapid development of information technology, the information security has received more and more attention. A variety of encryption methods to protect the information have been reported. Visual cryptography is one of the encryption methods, which has highly security because of its threshold feature. And the cryptographic information can be explained by a naked eye in the decryption process. In the application of visual cryptography, however, each shared image is limited to transparency films and overlapping on computer. In our previous work, we proposed the scheme of invisible visual cryptography and developed the visual-cryptography-based optical hiding system (VCOH), which transformed the conventional visual cryptography shares into diffraction optical elements (DOEs). It not only increases the application range of visual cryptography, but also enhances security. In this paper, we propose an optical information hiding system based on the extended visual cryptography, which inherits the concept of invisible visual cryptography. In contrast to our previous work, the method proposed in this work can hide a meaningful image instead of text messages. Meanwhile, the capacity and imperceptibility of the method are greatly increased. The hiding process of the system contains two steps. Firstly, the secret image is converted into meaningful shares through the extended visual cryptography algorithm. Secondly, the meaningful shares are able to hide in phase-keys through an iterative phase retrieval algorithm, such as Gerchberg-Saxton algorithm and Yang-Gu iterative algorithm. Then the phase-keys can be made into diffraction optical elements (DOEs) to store and transport in a physical way. In the decryption process, DOEs are illuminated with the laser beam to reconstruct the meaningful shares. The secret image can be explained by the direct overlapping of the reconstructed shares without any optical or cryptographic knowledge. The simulation and optical experimental results show that the proposed method has good performance of security and validate the feasibility of the proposed method. Besides, in this paper the robustness and security issues are also analyzed. This system has a high security because of its indistinguishability under adaptive chosen ciphertext attack (IND-CCA2) security. Additionally, this system is relatively less robust than the VCOH because it shares meaningful images with highly complex and detailed structures.
-
Keywords:
- optical hiding /
- extended visual cryptography /
- Fourier optics /
- phase-only keys
[1] Khan M, Shah T 2014 3 D Res. 5 29
 Google Scholar
Google Scholar
[2] Chen W, Javidi B, Chen X D 2014 Adv. Opt. Photonics 6 120
 Google Scholar
Google Scholar
[3] Liu S, Guo C L, Sheridan J T 2014 Opt. Laser Technol. 57 327
 Google Scholar
Google Scholar
[4] Shi Y S, Situ G H, Zhang J J 2007 Opt. Lett. 32 1914
 Google Scholar
Google Scholar
[5] Shi Y S, Situ G H, Zhang J J 2008 Opt. Lett. 33 542
 Google Scholar
Google Scholar
[6] 杨玉花, 史祎诗, 王雅丽, 肖俊, 张静娟 2011 60 034202
 Google Scholar
Google Scholar
Yang Y H, Shi Y S, Wang Y L, Xiao J, Zhang J J 2011 Acta Phys. Sin. 60 034202
 Google Scholar
Google Scholar
[7] Shi Y S, Li T, Wang Y L, Gao Q K, Zhang S G, Li H F 2013 Opt. Lett. 38 1425
 Google Scholar
Google Scholar
[8] Gao Q H, Wang Y L, Li T, Shi Y S 2014 Appl. Optics 53 4700
 Google Scholar
Google Scholar
[9] 刘祥磊, 潘泽, 王雅丽, 史祎诗 2015 64 234201
 Google Scholar
Google Scholar
Liu X L, Pan Z, Wang Y L, Shi Y S 2015 Acta Phys. Sin. 64 234201
 Google Scholar
Google Scholar
[10] Chanana A, Paulsen A, Guruswamy S, Nahata A 2016 Optica 3 1466
 Google Scholar
Google Scholar
[11] Xu W H, Xu H F, Luo Y, Li T, Shi Y S 2016 Opt. Express 24 27922
 Google Scholar
Google Scholar
[12] 姚丽莉, 袁操今, 强俊杰, 冯少彤, 聂守平 2016 65 214203
 Google Scholar
Google Scholar
Yao L L, Yuan C J, Qiang J J, Feng S T, Nie S P 2016 Acta Phys. Sin. 65 214203
 Google Scholar
Google Scholar
[13] Kong D Z, Shen X J, Cao L C, Jin G F 2017 Appl. Opt. 56 3449
 Google Scholar
Google Scholar
[14] Xu F H, Shulkind G, Thrampoulidis C, Shapiro J H, Torralba A, Wong F N C, Wornell Gr W 2018 Opt. Express 26 9945
 Google Scholar
Google Scholar
[15] Zhang L H, Yuan X, Zhang D W, Chen J 2018 Curr. Opt. Photon. 2 315
[16] 席思星, 于娜娜, 王晓雷, 朱巧芬, 董昭, 王微, 刘秀红, 王华英 2019 68 110502
 Google Scholar
Google Scholar
Xi S X, Yu N N, Wang X L, Zhu Q F, Dong Z, Wang W, Liu X H, Wang H Y 2019 Acta Phys. Sin. 68 110502
 Google Scholar
Google Scholar
[17] 王雪光, 李明, 于娜娜, 席思星, 王晓雷, 郎利影 2019 68 240503
 Google Scholar
Google Scholar
Wang X G, Li M, Yu N N, Xi S X, Wang X L, Lang L Y 2019 Acta Phys. Sin. 68 240503
 Google Scholar
Google Scholar
[18] Naor M, Shamir M 1994 Lect. Notes Comput. Sci. 950 1
 Google Scholar
Google Scholar
[19] Blundo C, Bonis A D, Santis A D 2001 Designs Codes Cryptogr. 24 255
 Google Scholar
Google Scholar
[20] Cimato S, Santis A D, Ferrara A L, Masucci B 2005 Inf. Process. Lett. 93 199
 Google Scholar
Google Scholar
[21] Blundo C, Santis A D, Naor M 2000 Inf. Proc. Lett. 75 255
 Google Scholar
Google Scholar
[22] Lin C C, Tsai W H 2003 Pattern Recognit. Lett. 24 349
 Google Scholar
Google Scholar
[23] Lukac R, Plataniotis K N 2005 Pattern Recognit. 38 767
 Google Scholar
Google Scholar
[24] Hou Y C 2003 Pattern Recognit. 36 1619
 Google Scholar
Google Scholar
[25] Yamamoto H, Hayasaki Y, Nishida N 2004 Opt. Express 12 1258
 Google Scholar
Google Scholar
[26] Machizaud J, Fournel T 2012 Opt. Express 20 22847
 Google Scholar
Google Scholar
[27] Wu H C, Chang C C 2005 Comput. Stand. Interfaces 28 123
 Google Scholar
Google Scholar
[28] Feng J B, Wu H C, Tsai C S, Chang Y F, Chu Y P 2008 Pattern Recognit. 41 3572
 Google Scholar
Google Scholar
[29] Mishra A, Gupta A 2018 J. Inf. and Optim. Sci. 39 631
[30] Blundo C, Cimato S, Santis A D 2006 Theor. Comput. Sci. 369 169
 Google Scholar
Google Scholar
[31] Chen Y F, Chan Y K, Huang C C, Tsai M H, Chu Y P 2007 Inf. Sci. 177 4696
 Google Scholar
Google Scholar
[32] Shi Y S, Yang X B 2017 J. Opt. 19 115703
 Google Scholar
Google Scholar
[33] Shi Y S, Yang X B 2017 Chin. Phys. Lett. 34 114204
 Google Scholar
Google Scholar
[34] Yang N, Gao Q K, Shi Y S 2018 Opt. Express 26 31995
 Google Scholar
Google Scholar
[35] Li Z F, Dong G Y, Yang D Y, Li G L, Shi Y S, Bi K, Zhou J 2019 Opt. Express 27 19212
 Google Scholar
Google Scholar
[36] Ateniese G, Blundo C, Santis A D, Stinson D R 2001 Theor. Comput. Sci. 250 143
 Google Scholar
Google Scholar
[37] Gerchberg R W, Saxton W O 1972 Optik 35 237
[38] 杨国桢, 顾本源 1981 30 410
 Google Scholar
Google Scholar
Yang G Z, Gu B Y 1981 Acta Phys. Sin. 30 410
 Google Scholar
Google Scholar
-
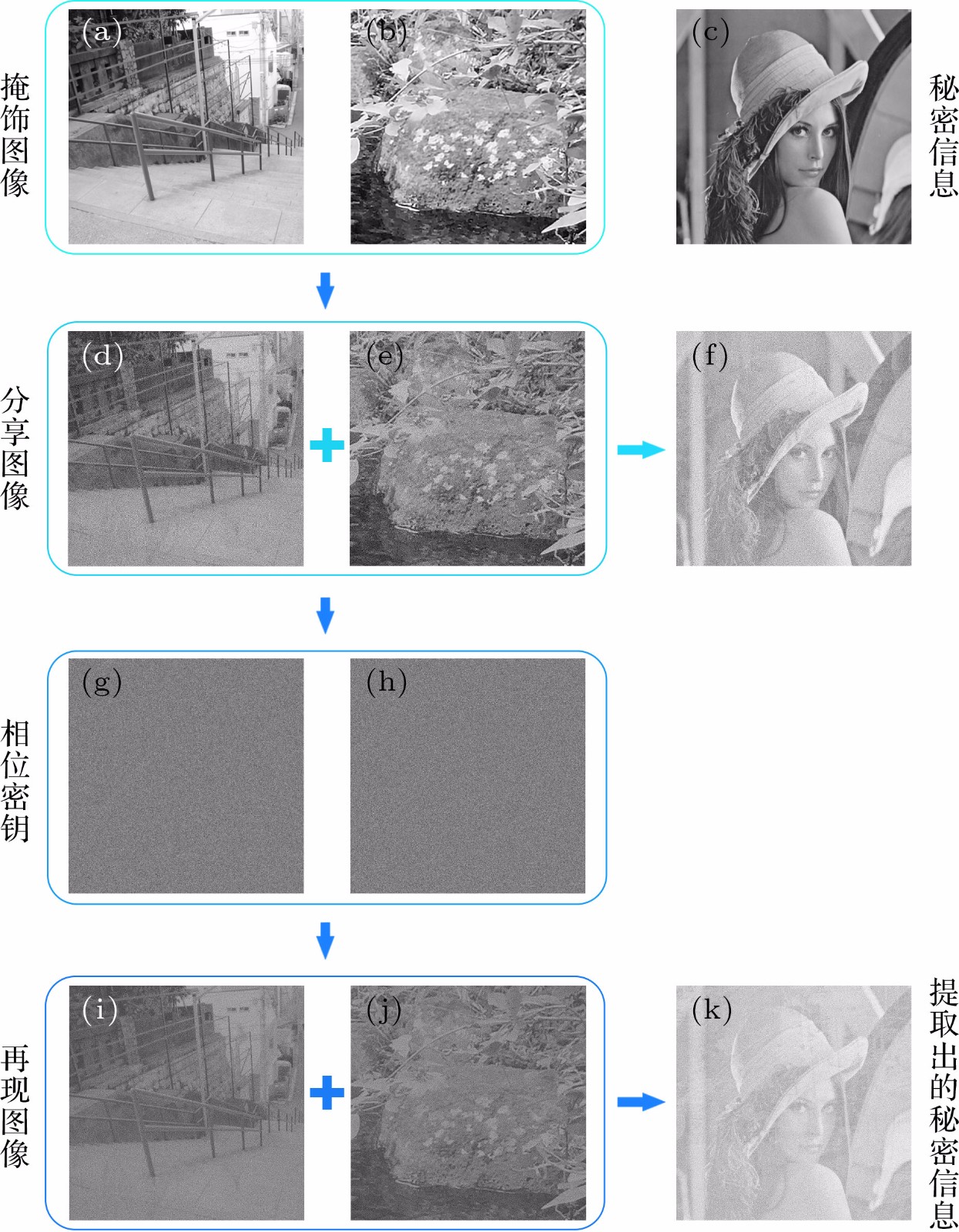
图 6 (a), (b)分享图像的掩饰图像; (c)秘密信息; (d), (e)编码后的分享图像; (f) (d), (e)叠加后的秘密信息; (g), (h)隐藏了分享图像的相位密钥; (i), (j)利用(g), (h)再现的分享图像; (k) (i), (j)非相干叠加后提取的秘密信息
Fig. 6. (a), (b) The original images of shares; (c) the secret image; (d), (e) the shares; (f) the secret images decrypted by stacked (d), (e) together; (g), (h) the phase keys; (i), (j) the reconstructed shares using (g), (h); (k) the recover secret images by stacking (i), (j) together
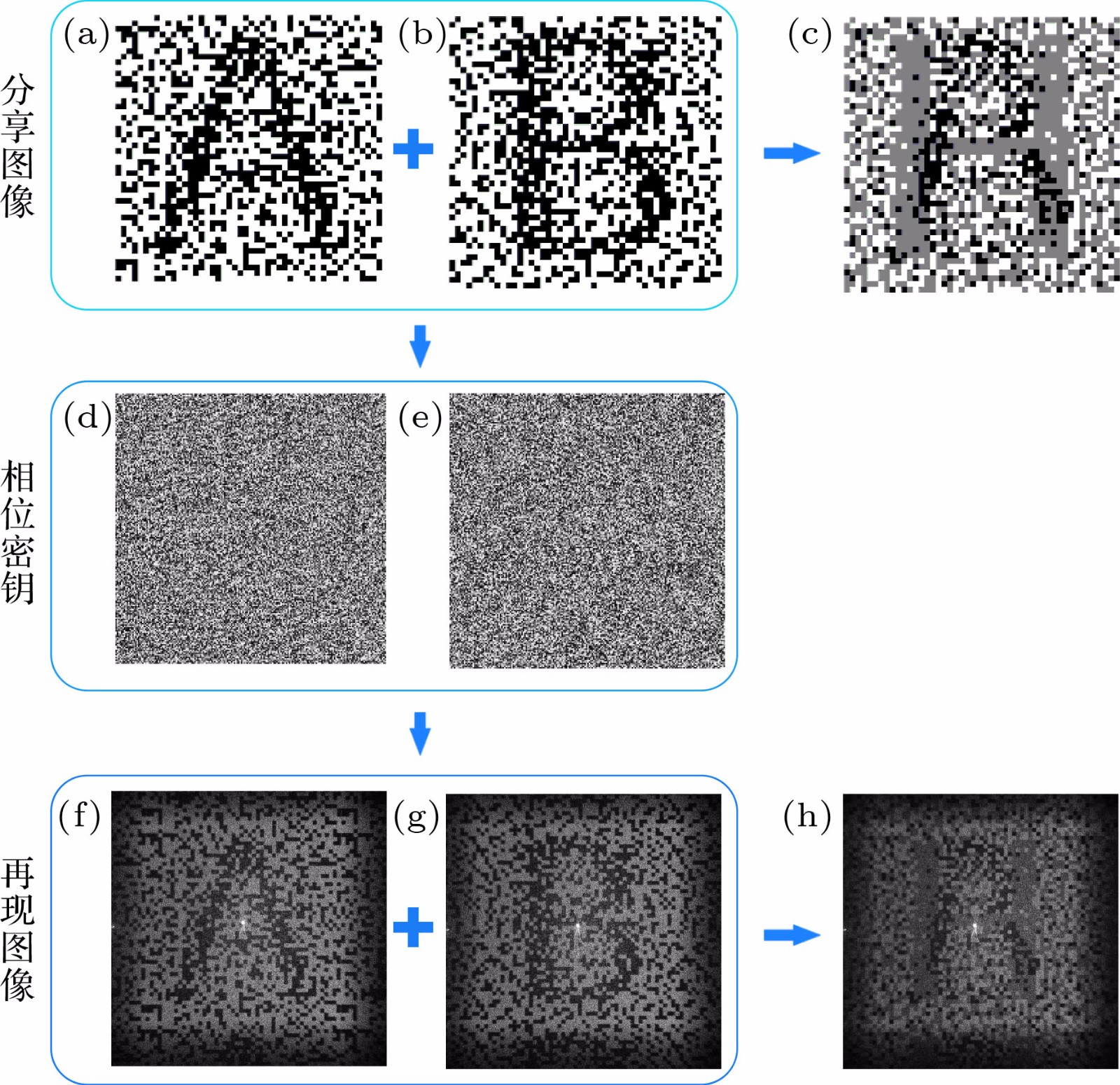
图 8 (a), (b)分享图像; (c) (a), (b)叠加后的秘密信息; (d), (e)隐藏了分享图像的相位密钥; (f), (g) CCD相机采集到的再现后分享图像; (h)非相干叠加后的秘密信息
Fig. 8. (a), (b) The shares, (c) the secret images decrypted by stacked (a), (b) together; (d), (e) the phase keys; (f), (g) the reconstructed shares that were taken with a CCD camera; (h) the recover secret images by stacking (f), (g) together
-
[1] Khan M, Shah T 2014 3 D Res. 5 29
 Google Scholar
Google Scholar
[2] Chen W, Javidi B, Chen X D 2014 Adv. Opt. Photonics 6 120
 Google Scholar
Google Scholar
[3] Liu S, Guo C L, Sheridan J T 2014 Opt. Laser Technol. 57 327
 Google Scholar
Google Scholar
[4] Shi Y S, Situ G H, Zhang J J 2007 Opt. Lett. 32 1914
 Google Scholar
Google Scholar
[5] Shi Y S, Situ G H, Zhang J J 2008 Opt. Lett. 33 542
 Google Scholar
Google Scholar
[6] 杨玉花, 史祎诗, 王雅丽, 肖俊, 张静娟 2011 60 034202
 Google Scholar
Google Scholar
Yang Y H, Shi Y S, Wang Y L, Xiao J, Zhang J J 2011 Acta Phys. Sin. 60 034202
 Google Scholar
Google Scholar
[7] Shi Y S, Li T, Wang Y L, Gao Q K, Zhang S G, Li H F 2013 Opt. Lett. 38 1425
 Google Scholar
Google Scholar
[8] Gao Q H, Wang Y L, Li T, Shi Y S 2014 Appl. Optics 53 4700
 Google Scholar
Google Scholar
[9] 刘祥磊, 潘泽, 王雅丽, 史祎诗 2015 64 234201
 Google Scholar
Google Scholar
Liu X L, Pan Z, Wang Y L, Shi Y S 2015 Acta Phys. Sin. 64 234201
 Google Scholar
Google Scholar
[10] Chanana A, Paulsen A, Guruswamy S, Nahata A 2016 Optica 3 1466
 Google Scholar
Google Scholar
[11] Xu W H, Xu H F, Luo Y, Li T, Shi Y S 2016 Opt. Express 24 27922
 Google Scholar
Google Scholar
[12] 姚丽莉, 袁操今, 强俊杰, 冯少彤, 聂守平 2016 65 214203
 Google Scholar
Google Scholar
Yao L L, Yuan C J, Qiang J J, Feng S T, Nie S P 2016 Acta Phys. Sin. 65 214203
 Google Scholar
Google Scholar
[13] Kong D Z, Shen X J, Cao L C, Jin G F 2017 Appl. Opt. 56 3449
 Google Scholar
Google Scholar
[14] Xu F H, Shulkind G, Thrampoulidis C, Shapiro J H, Torralba A, Wong F N C, Wornell Gr W 2018 Opt. Express 26 9945
 Google Scholar
Google Scholar
[15] Zhang L H, Yuan X, Zhang D W, Chen J 2018 Curr. Opt. Photon. 2 315
[16] 席思星, 于娜娜, 王晓雷, 朱巧芬, 董昭, 王微, 刘秀红, 王华英 2019 68 110502
 Google Scholar
Google Scholar
Xi S X, Yu N N, Wang X L, Zhu Q F, Dong Z, Wang W, Liu X H, Wang H Y 2019 Acta Phys. Sin. 68 110502
 Google Scholar
Google Scholar
[17] 王雪光, 李明, 于娜娜, 席思星, 王晓雷, 郎利影 2019 68 240503
 Google Scholar
Google Scholar
Wang X G, Li M, Yu N N, Xi S X, Wang X L, Lang L Y 2019 Acta Phys. Sin. 68 240503
 Google Scholar
Google Scholar
[18] Naor M, Shamir M 1994 Lect. Notes Comput. Sci. 950 1
 Google Scholar
Google Scholar
[19] Blundo C, Bonis A D, Santis A D 2001 Designs Codes Cryptogr. 24 255
 Google Scholar
Google Scholar
[20] Cimato S, Santis A D, Ferrara A L, Masucci B 2005 Inf. Process. Lett. 93 199
 Google Scholar
Google Scholar
[21] Blundo C, Santis A D, Naor M 2000 Inf. Proc. Lett. 75 255
 Google Scholar
Google Scholar
[22] Lin C C, Tsai W H 2003 Pattern Recognit. Lett. 24 349
 Google Scholar
Google Scholar
[23] Lukac R, Plataniotis K N 2005 Pattern Recognit. 38 767
 Google Scholar
Google Scholar
[24] Hou Y C 2003 Pattern Recognit. 36 1619
 Google Scholar
Google Scholar
[25] Yamamoto H, Hayasaki Y, Nishida N 2004 Opt. Express 12 1258
 Google Scholar
Google Scholar
[26] Machizaud J, Fournel T 2012 Opt. Express 20 22847
 Google Scholar
Google Scholar
[27] Wu H C, Chang C C 2005 Comput. Stand. Interfaces 28 123
 Google Scholar
Google Scholar
[28] Feng J B, Wu H C, Tsai C S, Chang Y F, Chu Y P 2008 Pattern Recognit. 41 3572
 Google Scholar
Google Scholar
[29] Mishra A, Gupta A 2018 J. Inf. and Optim. Sci. 39 631
[30] Blundo C, Cimato S, Santis A D 2006 Theor. Comput. Sci. 369 169
 Google Scholar
Google Scholar
[31] Chen Y F, Chan Y K, Huang C C, Tsai M H, Chu Y P 2007 Inf. Sci. 177 4696
 Google Scholar
Google Scholar
[32] Shi Y S, Yang X B 2017 J. Opt. 19 115703
 Google Scholar
Google Scholar
[33] Shi Y S, Yang X B 2017 Chin. Phys. Lett. 34 114204
 Google Scholar
Google Scholar
[34] Yang N, Gao Q K, Shi Y S 2018 Opt. Express 26 31995
 Google Scholar
Google Scholar
[35] Li Z F, Dong G Y, Yang D Y, Li G L, Shi Y S, Bi K, Zhou J 2019 Opt. Express 27 19212
 Google Scholar
Google Scholar
[36] Ateniese G, Blundo C, Santis A D, Stinson D R 2001 Theor. Comput. Sci. 250 143
 Google Scholar
Google Scholar
[37] Gerchberg R W, Saxton W O 1972 Optik 35 237
[38] 杨国桢, 顾本源 1981 30 410
 Google Scholar
Google Scholar
Yang G Z, Gu B Y 1981 Acta Phys. Sin. 30 410
 Google Scholar
Google Scholar
计量
- 文章访问数: 9560
- PDF下载量: 129
- 被引次数: 0













 下载:
下载: