-
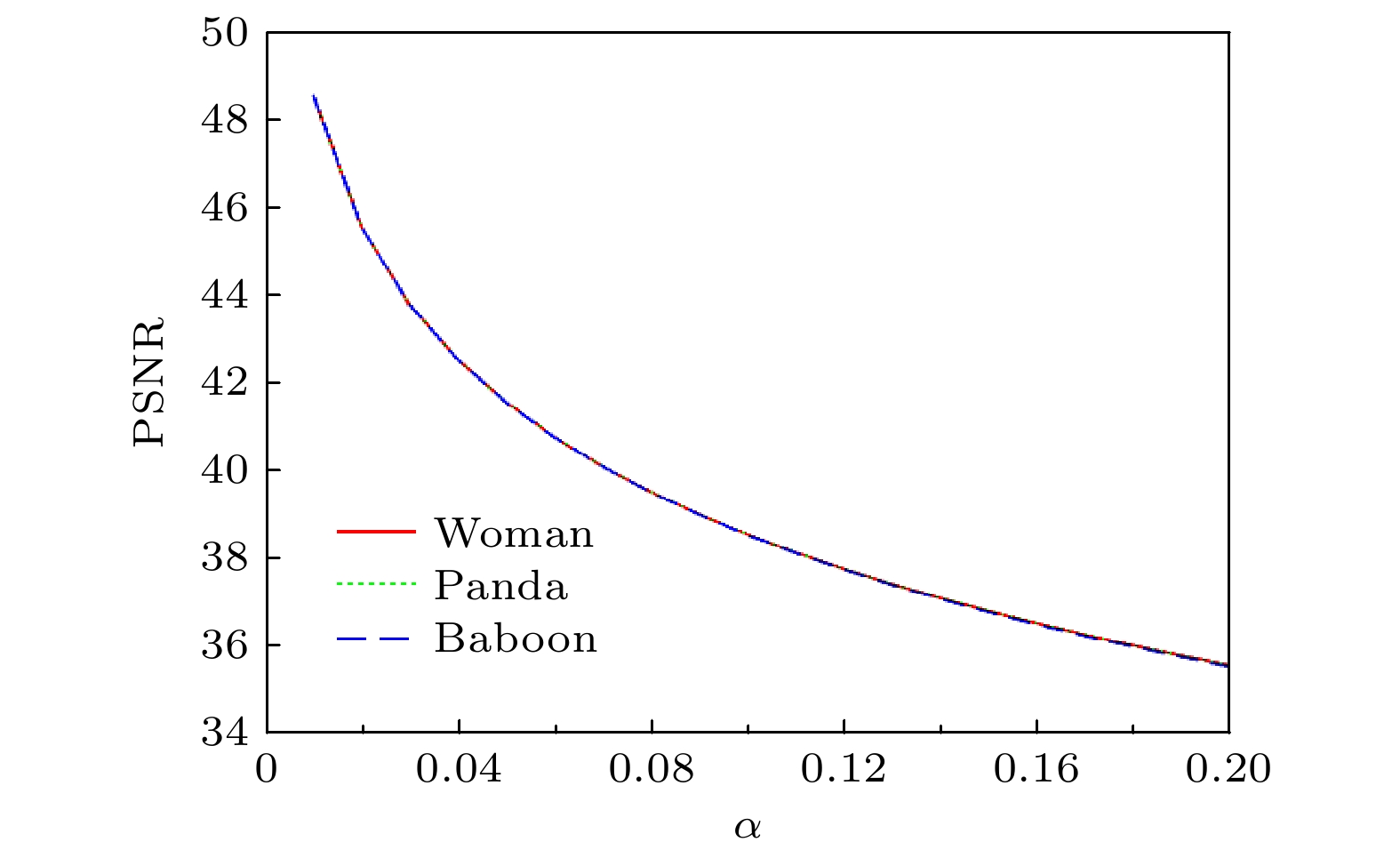
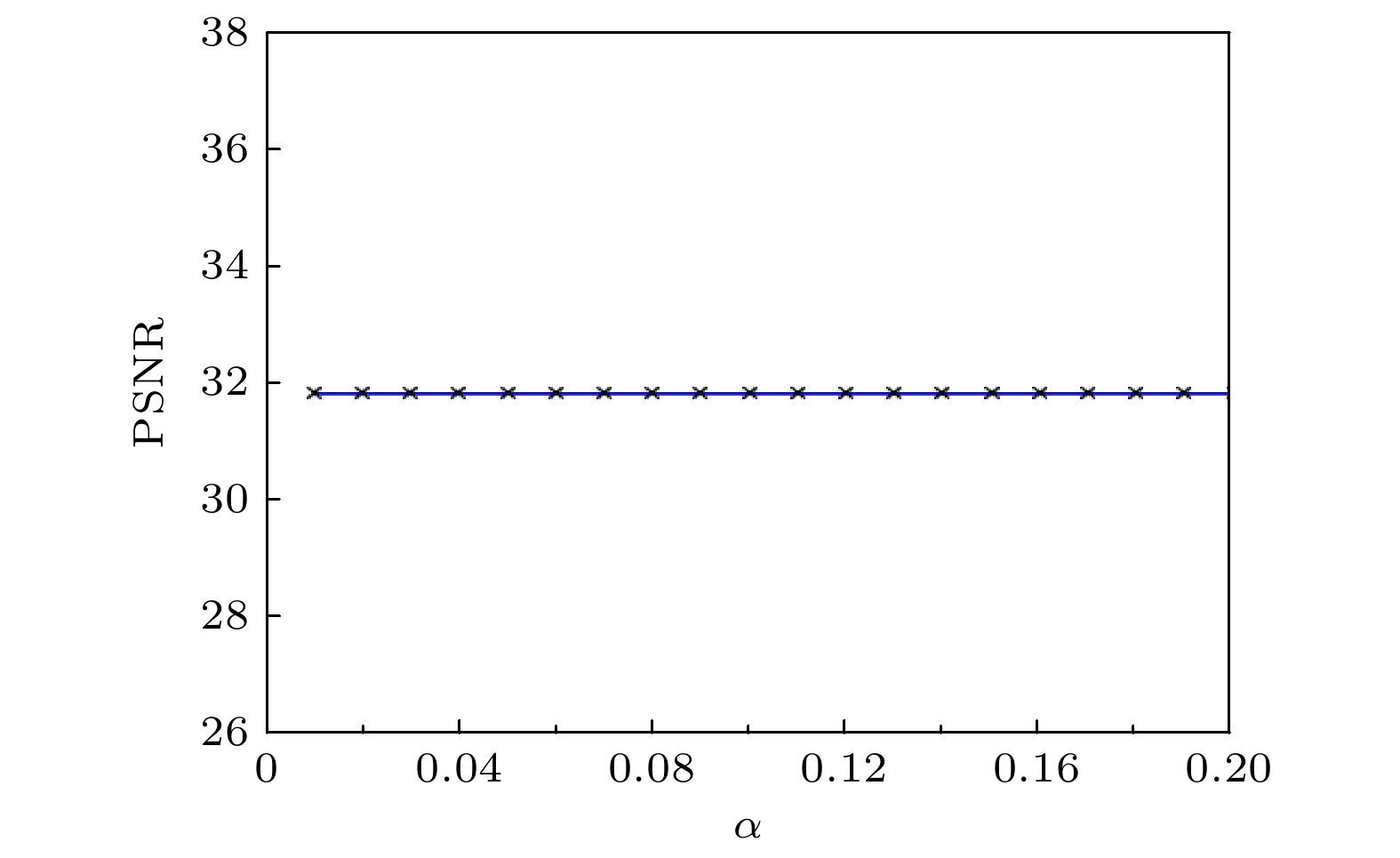
An optical fragile watermarking method is proposed based on visual cryptography and QR code for image authentication and tamper detection. On the one hand, the original image is transformed into a QR watermark image to improve the watermark hiding capacity. On the other hand, the visual cryptography and optical phase coding are fused to encrypt the watermark image to enhance system security. The feasibility, vulnerability and imperceptibility of the proposed scheme are tested through a series of attacks and tampering. The simulation results show that the proposed method can not only have good imperceptibility, but also achieve high detection performance under different attacks and tampering.
-
Keywords:
- optical fragile watermarking /
- visual cryptography /
- QR code /
- tamper detection
[1] Thanki, Rohit 2021 Int. J. Digit. Crime Forensics 13 35
 Google Scholar
Google Scholar
[2] 余朔望 2013 中国信息化 8 204
Yu S W 2013 iChina 8 204
[3] Bravo-Solorio S, Nandi A K 2011 Signal Process. 91 728
 Google Scholar
Google Scholar
[4] Chen Z Y 2013 Signal Process. Image Commun. 28 301
 Google Scholar
Google Scholar
[5] 郑秋梅, 刘楠 2020 计算机科学 47 332
 Google Scholar
Google Scholar
Zheng Q M, Liu N 2020 Comput. Sci. 47 332
 Google Scholar
Google Scholar
[6] Ruan T, Yang D, Shi Y 2021 Appl. Opt. 60 3071
 Google Scholar
Google Scholar
[7] Shi Y, Li T, Wang Y, Gao Q, Zhang S, Li H 2013 Opt. Lett. 38 1425
 Google Scholar
Google Scholar
[8] 刘祥磊, 潘泽, 王雅丽, 史祎诗 2015 23 234201
 Google Scholar
Google Scholar
Liu X L, Pan Z, Wang Y L, Shi Y S 2015 Acta Phys. Sin. 23 234201
 Google Scholar
Google Scholar
[9] Xu W H, Xu H F, Luo Y, Li T 2016 Opt. Express 24 27922
 Google Scholar
Google Scholar
[10] Li C, Wang Y, Ma B, Zhang Z 2012 Comput. Stand. Interfaces 34 367
 Google Scholar
Google Scholar
[11] Shi Y S, Yang X 2017 J. Opt. 19 115703
 Google Scholar
Google Scholar
[12] 曾高荣, 裘正定 2010 59 5870
 Google Scholar
Google Scholar
Zeng G R, Qiu Z D 2010 Acta Phys. Sin 59 5870
 Google Scholar
Google Scholar
[13] Ma R, Li Y, Jia H Z, Shi Y S, Xie X D, Huang T J 2021 Opt. Lasers Eng. 141 106569
 Google Scholar
Google Scholar
[14] Zhu Y P, Xu W H, Shi Y S 2019 Opt. Commun. 435 426
 Google Scholar
Google Scholar
[15] Lv W J, Sun X K, Yang D Y, Zhu Y P, Tao Y, Shi Y S 2021 Opt. Lasers Eng. 141 106574
 Google Scholar
Google Scholar
[16] 于韬, 杨栋宇, 马锐, 史祎诗 2020 69 144202
 Google Scholar
Google Scholar
Yu T, Yang D Y, Ma R, Shi Y S 2020 Acta Phys. Sin 69 144202
 Google Scholar
Google Scholar
[17] Yang N, GAO Q K, Shi Y S 2018 Opt. Express 26 31995
 Google Scholar
Google Scholar
[18] Li Z F, Dong G Y, Yang D Y, Li G L, Shi Y S, Bi K, Zhou J 2019 Opt. Express 27 19212
 Google Scholar
Google Scholar
[19] Sun X K, Zhang S G, Ma R, Tao Y, Zhu Y P, Yang D Y, Shi Y S 2020 Opt. Express 28 31832
 Google Scholar
Google Scholar
[20] Jiao S M, Zhou C Y, Shi Y S, Zou W B, Li X 2019 Opt. Laser Technol. 109 370
 Google Scholar
Google Scholar
[21] Xu R Q, Lv P, Xu F J, Shi Y S 2021 Opt. Laser Technol. 136 106787
 Google Scholar
Google Scholar
[22] Refregier P, Bahram B 1995 Opt. Lett. 20 767
 Google Scholar
Google Scholar
[23] Kishk S, Javidi B 2002 Appl. Opt. 41 5462
 Google Scholar
Google Scholar
-
图 1 光学水印生成与嵌入过程
Fig. 1. Optical watermark generation and embedding process. (I) is the process of transforming the original image into a QR code and encoding it through visual-cryptographic (VC denotes visual- cryptography encoding). (II) is the process of optical phase encryption. (III) is the embedding process of watermark.
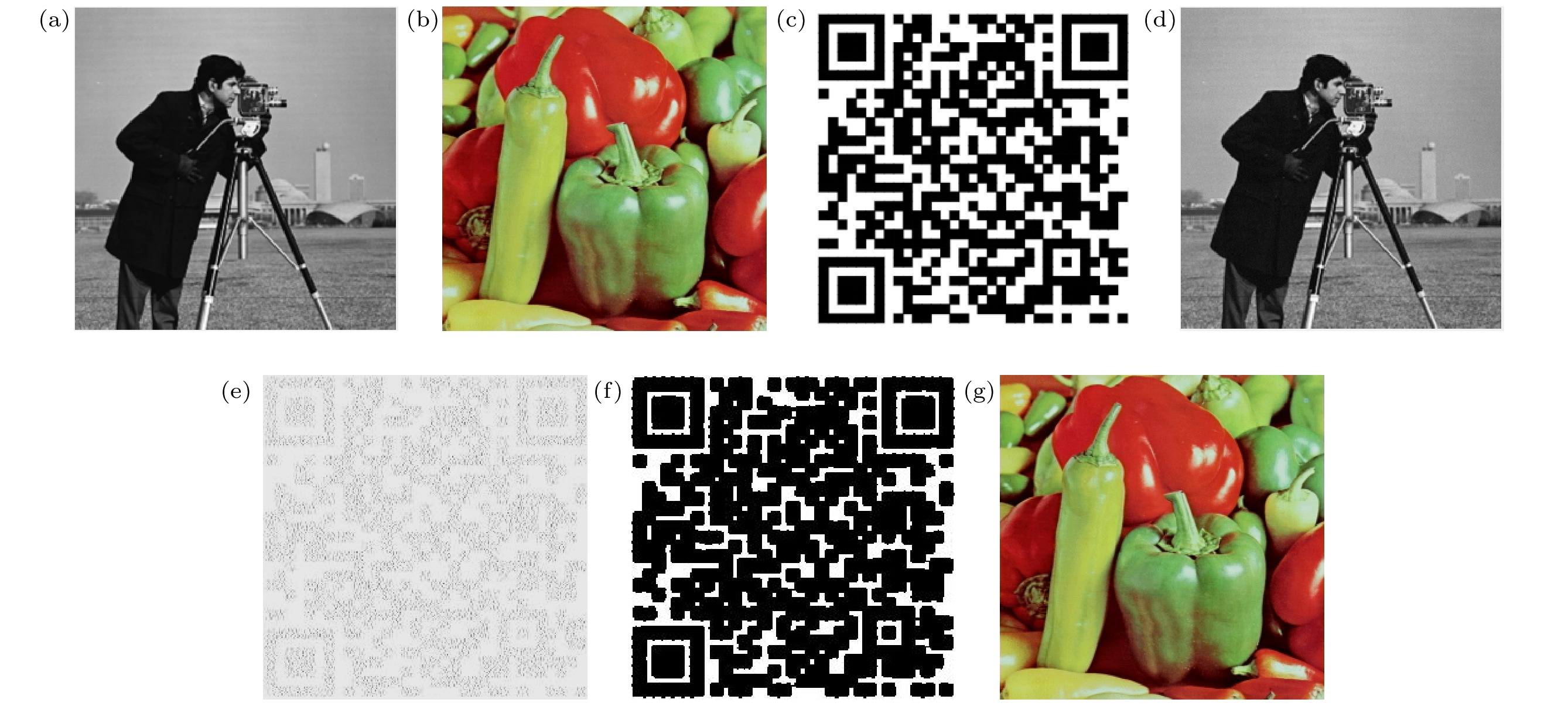
图 3 未受到任何攻击与篡改的水印提取结果 (a) 宿主图像; (b)原始水印图像; (c)由原始水印图像生成的QR码水印图像; (d) 嵌入水印后的图像; (e) 无任何攻击和篡改, 且使用正确密钥提取出来的水印图像; (f)腐蚀膨胀处理后的QR码水印图像; (g)使用移动设备扫描得到的原始水印图像
Fig. 3. Watermark extraction results without any attack and tampering: (a) Host image; (b) original watermark image; (c) QR code watermark image generated from original watermark image; (d) watermarked image; (e) watermark image without any attack or tampering, and using the correct key to extract the watermark; (f) QR code watermark image after corrosion expansion; (g) original watermark image scanned by mobile device.
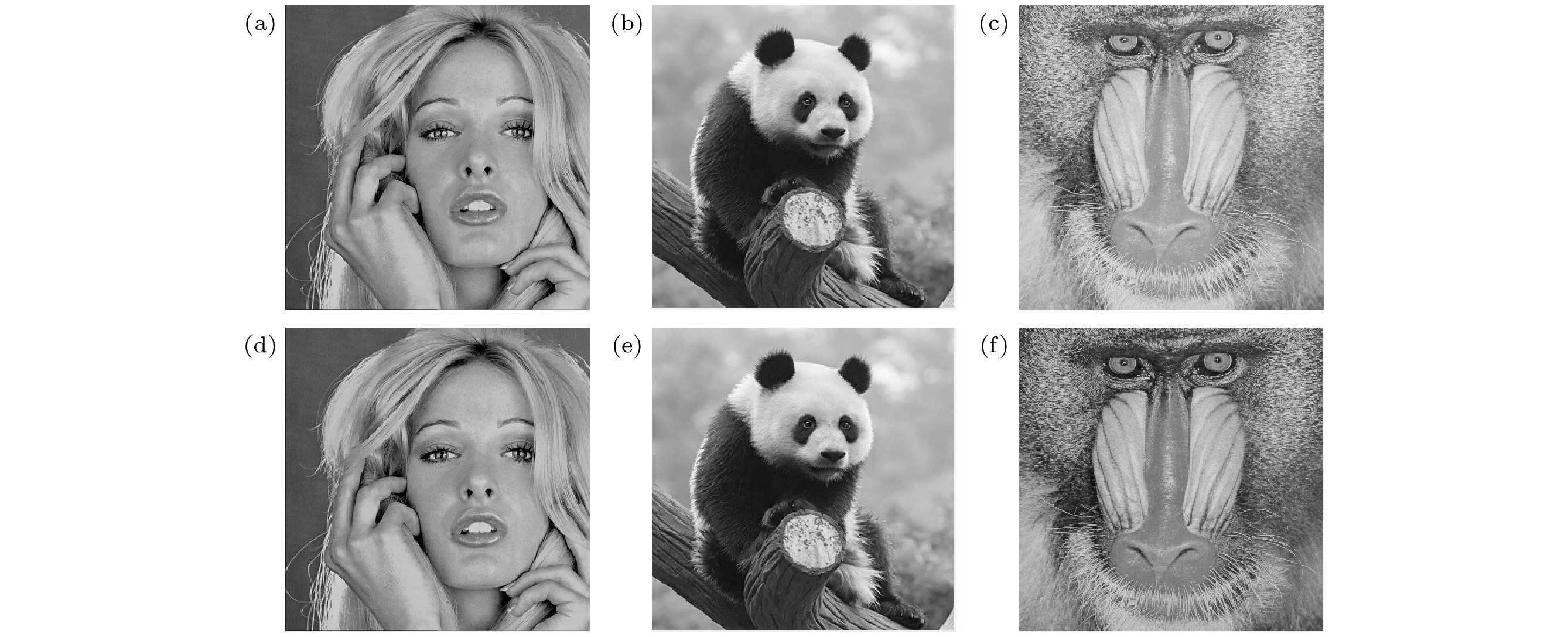
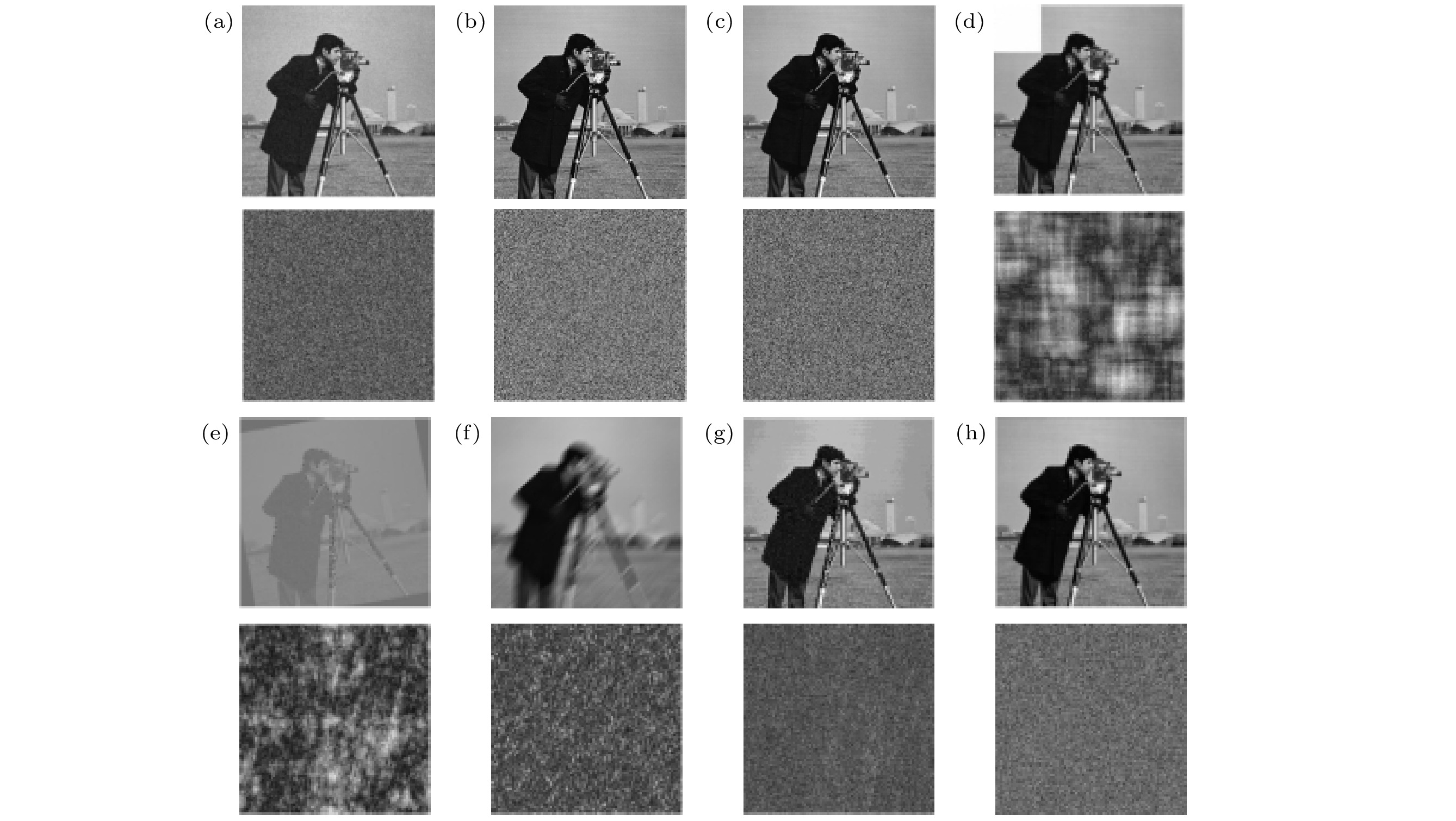
图 10 常见攻击下的水印提取结果 (a)−(c)高斯噪声攻击、椒盐噪声攻击、斑点噪声攻击; (d)−(h)剪切、旋转、运动模糊、JPEG压缩、高斯低通滤波
Fig. 10. Results of common attacks for watermarked images: (a)−(c) Gaussian noise attack, salt and pepper noise attack, speckle noise attack; (d)−(h) shear, rotation, motion blur, JPEG compression, gaussian low pass filtering.
-
[1] Thanki, Rohit 2021 Int. J. Digit. Crime Forensics 13 35
 Google Scholar
Google Scholar
[2] 余朔望 2013 中国信息化 8 204
Yu S W 2013 iChina 8 204
[3] Bravo-Solorio S, Nandi A K 2011 Signal Process. 91 728
 Google Scholar
Google Scholar
[4] Chen Z Y 2013 Signal Process. Image Commun. 28 301
 Google Scholar
Google Scholar
[5] 郑秋梅, 刘楠 2020 计算机科学 47 332
 Google Scholar
Google Scholar
Zheng Q M, Liu N 2020 Comput. Sci. 47 332
 Google Scholar
Google Scholar
[6] Ruan T, Yang D, Shi Y 2021 Appl. Opt. 60 3071
 Google Scholar
Google Scholar
[7] Shi Y, Li T, Wang Y, Gao Q, Zhang S, Li H 2013 Opt. Lett. 38 1425
 Google Scholar
Google Scholar
[8] 刘祥磊, 潘泽, 王雅丽, 史祎诗 2015 23 234201
 Google Scholar
Google Scholar
Liu X L, Pan Z, Wang Y L, Shi Y S 2015 Acta Phys. Sin. 23 234201
 Google Scholar
Google Scholar
[9] Xu W H, Xu H F, Luo Y, Li T 2016 Opt. Express 24 27922
 Google Scholar
Google Scholar
[10] Li C, Wang Y, Ma B, Zhang Z 2012 Comput. Stand. Interfaces 34 367
 Google Scholar
Google Scholar
[11] Shi Y S, Yang X 2017 J. Opt. 19 115703
 Google Scholar
Google Scholar
[12] 曾高荣, 裘正定 2010 59 5870
 Google Scholar
Google Scholar
Zeng G R, Qiu Z D 2010 Acta Phys. Sin 59 5870
 Google Scholar
Google Scholar
[13] Ma R, Li Y, Jia H Z, Shi Y S, Xie X D, Huang T J 2021 Opt. Lasers Eng. 141 106569
 Google Scholar
Google Scholar
[14] Zhu Y P, Xu W H, Shi Y S 2019 Opt. Commun. 435 426
 Google Scholar
Google Scholar
[15] Lv W J, Sun X K, Yang D Y, Zhu Y P, Tao Y, Shi Y S 2021 Opt. Lasers Eng. 141 106574
 Google Scholar
Google Scholar
[16] 于韬, 杨栋宇, 马锐, 史祎诗 2020 69 144202
 Google Scholar
Google Scholar
Yu T, Yang D Y, Ma R, Shi Y S 2020 Acta Phys. Sin 69 144202
 Google Scholar
Google Scholar
[17] Yang N, GAO Q K, Shi Y S 2018 Opt. Express 26 31995
 Google Scholar
Google Scholar
[18] Li Z F, Dong G Y, Yang D Y, Li G L, Shi Y S, Bi K, Zhou J 2019 Opt. Express 27 19212
 Google Scholar
Google Scholar
[19] Sun X K, Zhang S G, Ma R, Tao Y, Zhu Y P, Yang D Y, Shi Y S 2020 Opt. Express 28 31832
 Google Scholar
Google Scholar
[20] Jiao S M, Zhou C Y, Shi Y S, Zou W B, Li X 2019 Opt. Laser Technol. 109 370
 Google Scholar
Google Scholar
[21] Xu R Q, Lv P, Xu F J, Shi Y S 2021 Opt. Laser Technol. 136 106787
 Google Scholar
Google Scholar
[22] Refregier P, Bahram B 1995 Opt. Lett. 20 767
 Google Scholar
Google Scholar
[23] Kishk S, Javidi B 2002 Appl. Opt. 41 5462
 Google Scholar
Google Scholar
计量
- 文章访问数: 5794
- PDF下载量: 86
- 被引次数: 0














 下载:
下载: