-
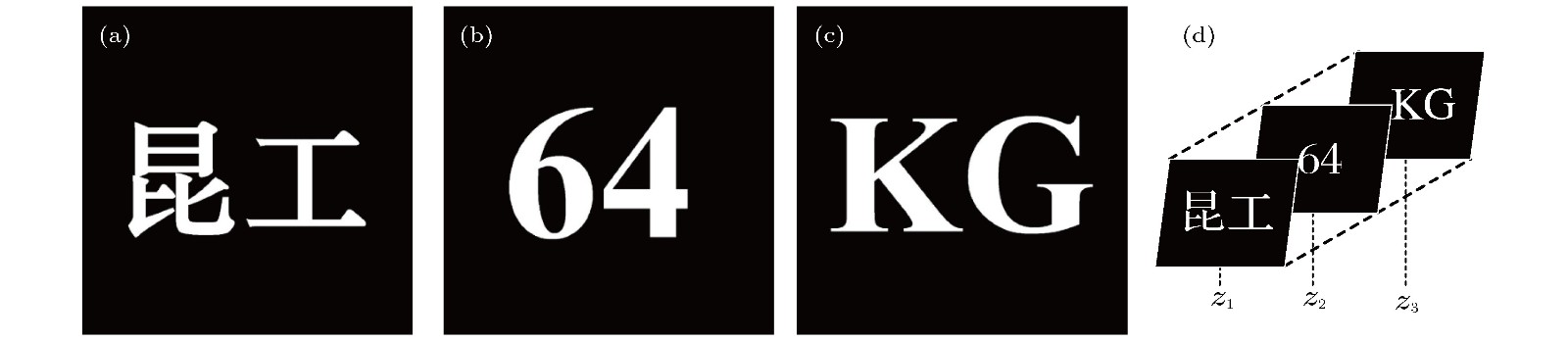
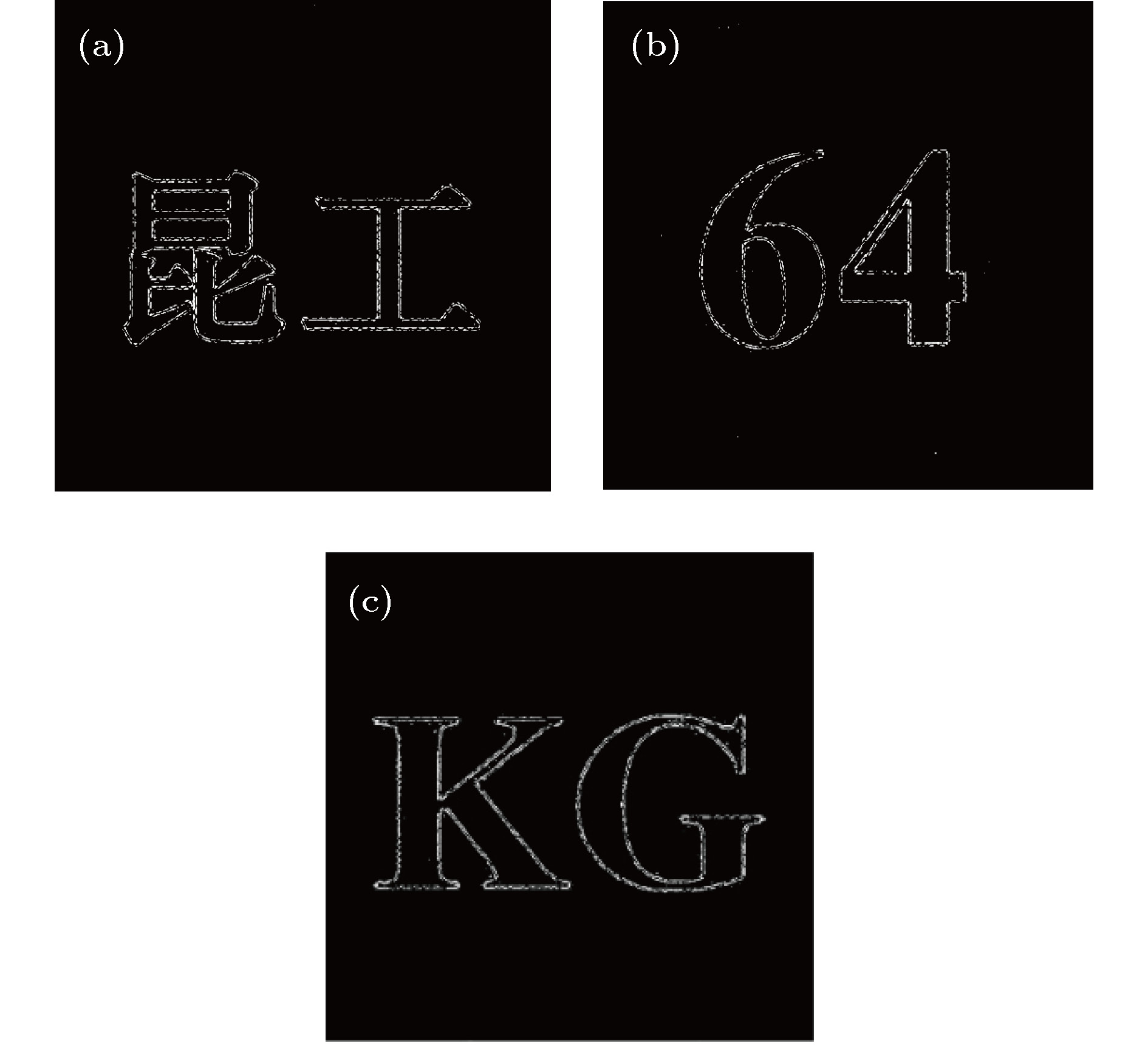
In this paper, the function of parallel encrypting multiple images and reproducing arbitrary layers of images is realized by improving the double pupil function in optical scanning holography. In an optical scanning holography (OSH) system, a dual-pupil heterodyne incoherent image processing technique is used to record holographic images. By adjusting the two pupil functions in the optical system, the interference fringes can be modified to achieve different imaging effects. In this paper, the ring pupil and random phase plate are used to act as two pupil functions to interfere to form a ring random phase plate, and thus realizing the fast scanning of multi-layer images. Then the multi-layer images can be quickly encrypted by one imaging technique. The scanned signals are quickly collected by photoelectric detectors, and they synthesize encrypted holograms by computer. By using the digital holography to decrypt the holograms, the precise reproduction of any layer image can be achieved. The OSH system with random phase pupil is strongly dependent on the longitudinal position of the system in digital reconstruction. The defocusing noise can be converted into random noise and the effect of defocusing layer on imaging can be effectively suppressed. However, in practice, it is necessary to average multiple images to achieve better imaging effect, and the accuracy of random phase plate is required. In this paper, most of the random noise can be filtered with the aid of ring pupil, and all the information about multi-layer graphics can be recorded and reconstructed by one scan. In the process of reconstruction, the influence of defocusing image can be effectively eliminated, and the decryption of any layer image can be realized. This method collects encrypted image by photoelectric detector, and does not need complex algorithm reconstruction nor phase iteration, which greatly reduces the time expended in the encryption process. In the process of encryption, the key space of the system is increased, and the encrypted image obtained has high security. In this paper, correlation coefficient is used to evaluate the encryption effect of this method, and the effectiveness and security of this method are verified by simulation experiments. For cutting resistance, when 75% of the information is lost, the correlation coefficient can still reach more than 0.5. For the sensitivity of information, the integrity of decrypted image will be seriously damaged when the wavelength and distance shift very little. For the anti-noise ability, under the influence of Gauss noise and salt and pepper noise, the correlation coefficient and image recognition degree are high. This method is very time-saving, and the result of encryption has high security, high sensitivity, strong ability to resist clipping and noise.
-
Keywords:
- optical scanning holography /
- optical parallel encryption /
- annular pupil /
- random phase plate
[1] Qin W, Peng X 2010 Opt. Lett. 35 118
 Google Scholar
Google Scholar
[2] Tsang P, Cheung K W K, Poon T C 2013 Chin. Opt. Lett. 11 27
[3] Unnikrishnan G, Joseph J, Singh K 2000 Opt. Lett. 25 887
 Google Scholar
Google Scholar
[4] Zhou N, Wang Y, He H, Gong L, Wu J 2011 Opt. Commun. 284 2789
 Google Scholar
Google Scholar
[5] Alfalou A, Brosseau C 2009 Adv. Opt. Photonics 1 589
 Google Scholar
Google Scholar
[6] Zhang Y, Wang B 2008 Opt. Lett. 33 2443
 Google Scholar
Google Scholar
[7] 姚丽莉, 袁操今, 强俊杰, 冯少彤, 聂守平 2016 65 214203
 Google Scholar
Google Scholar
Yao L L, Yuan C J, Qiang J J, Feng S T, Nie S P 2016 Acta Phys. Sin 65 214203
 Google Scholar
Google Scholar
[8] Refregier P, Javidi B 1995 Opt. Lett. 20 67
 Google Scholar
Google Scholar
[9] Takai N, Mifune Y 2002 Appl. Opt. 41 865
 Google Scholar
Google Scholar
[10] Matoba O, Javidi B 2004 Appl. Opt. 43 2915
 Google Scholar
Google Scholar
[11] Wu J H, Luo X Z, Zhou N R 2013 Opt. Laser Technol. 45 571
 Google Scholar
Google Scholar
[12] He M Z, Cai L Z, Liu Q, Wang X C, Meng X F 2005 Opt. Commun. 247 29
 Google Scholar
Google Scholar
[13] Situ G, Zhang J 2005 Opt. Lett. 30 1306
 Google Scholar
Google Scholar
[14] Qin Y, Gong Q 2013 Appl. Opt. 52 3987
 Google Scholar
Google Scholar
[15] Tajahuerce E, Matoba O, Verrall S C, Javidi B 2000 Appl. Opt. 39 2313
 Google Scholar
Google Scholar
[16] Carnicer A, Montes-Usategui M, Arcos S, Juvells I 2005 Opt. Lett. 30 1644
 Google Scholar
Google Scholar
[17] Peng X, Zhang P, Wei H, Yu B 2006 Opt. Lett. 31 1044
 Google Scholar
Google Scholar
[18] Poon T C, Korpel A 1979 Opt. Lett. 4 317
 Google Scholar
Google Scholar
[19] Poon T C 2009 J. Opt. Soc. Korea 13 406
 Google Scholar
Google Scholar
[20] Poon T C 2007 Optical Scanning Holography with MATLAB (Verlag: Springer) pp66−92
[21] Poon T C 1985 J. Opt. Soc. Am. A 2 521
 Google Scholar
Google Scholar
[22] Pan Y J, Jia W, Yu J J, Dobson K, Zhou C H, Wang Y T, Poon T C 2014 Opt. Lett 39 4176
 Google Scholar
Google Scholar
[23] Poon T C, Kim T, Doh K 2003 Appl. Opt 42 6496
 Google Scholar
Google Scholar
[24] Zhou X, Dobson K, Shinoda Y, Poon T C 2010 Opt. Lett 35 2934
 Google Scholar
Google Scholar
[25] 王仁德, 张亚萍, 王帆, 祝旭锋, 李重光, 张永安, 许蔚 2019 中国激光 46 0109001
Wang R D, Zhang Y P, Wang F, Zhu X F, Li C G, Zhang Y A, Xu W 2019 Chin. J. Laser 46 0109001
[26] Wang B, Zhang Y 2009 Opt. Commun. 282 3439
 Google Scholar
Google Scholar
[27] Chen W, Chen, X 2011 J. Opt. 13 115401
 Google Scholar
Google Scholar
-
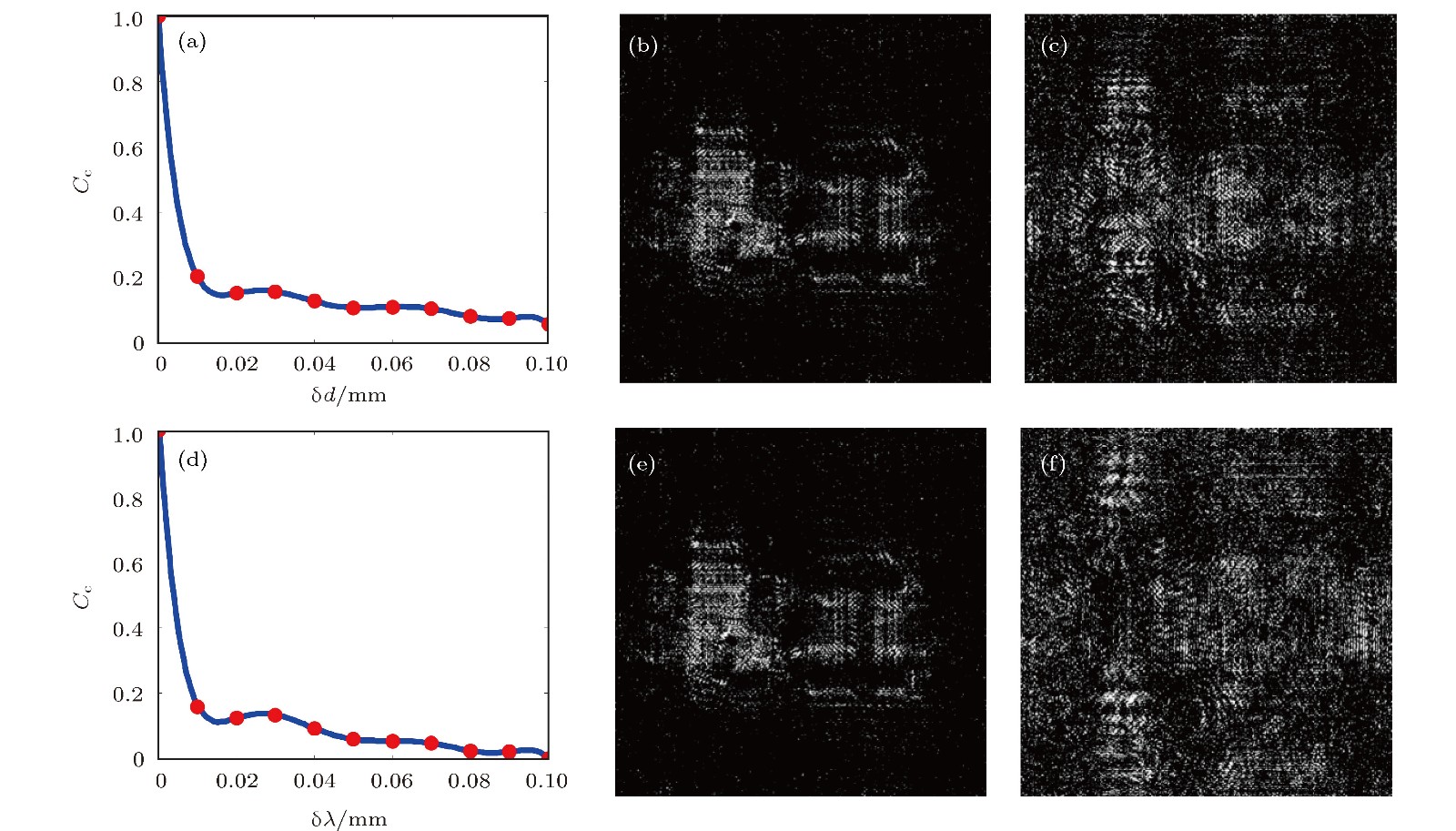
图 7 错误解密结果 (a) 相关系数Cc随δd变化的曲线图; (b) 和 (c) δd = 0.01和0.1 mm时的解密结果; (d) 相关系数Cc随δλ变化的曲线图; (e) 和 (f) δλ = 0.1和1 nm时的解密结果
Fig. 7. Incorrect decryption results: (a) The Cc curve of varies with δd; (b) and (c) decryption result of δd = 0.1 and 0.1 mm, respectively; (d) the Cc curve of varies with δλ; (e) and (f) decryption result of δλ = 0.1 and 1 nm, respectively.
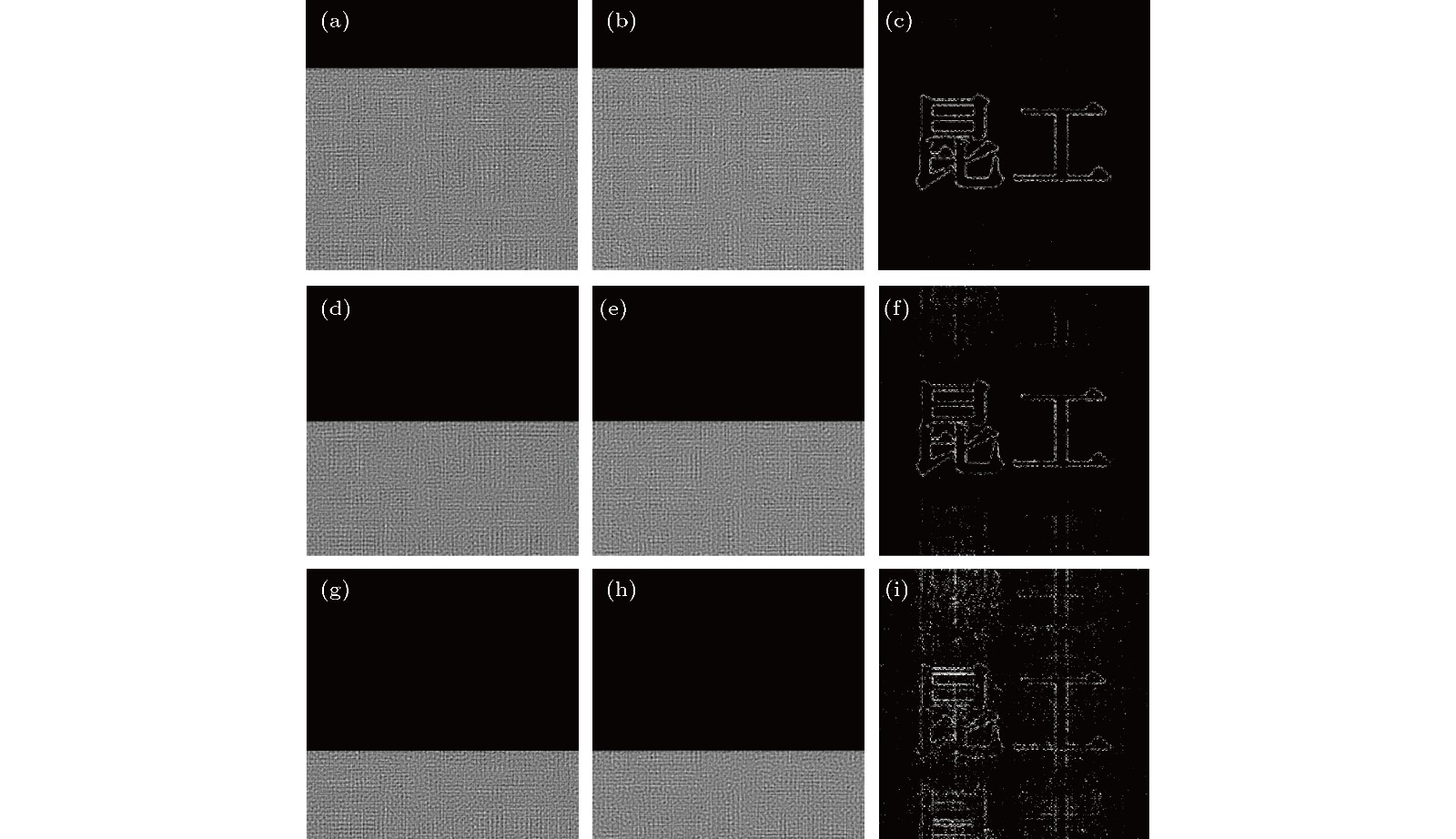
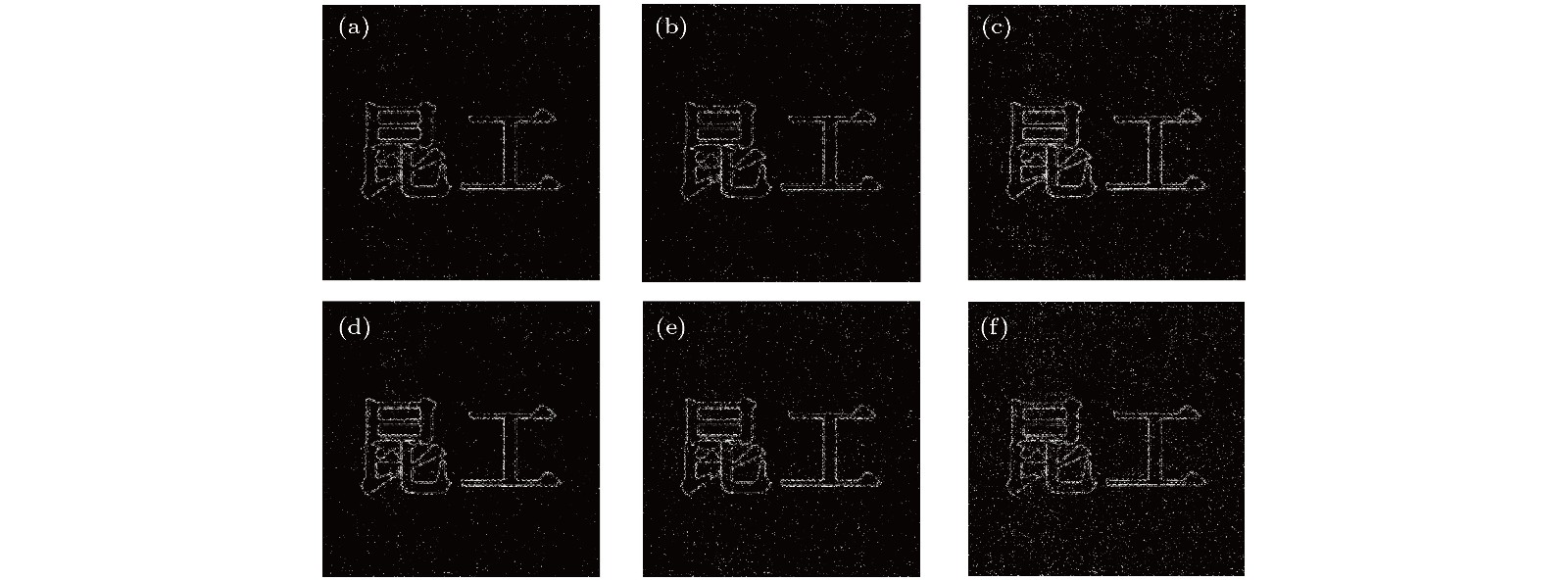
图 9 抗剪裁性能模拟结果 (a) 和 (b) 信息丢失25%的正余弦加密图像; (c) 信息丢失25%后的解密结果; (d) 和 (e) 信息丢失50%的正余弦加密图像; (f) 信息丢失50%后的解密结果; (g) 和 (h) 信息丢失75%的正余弦加密图像; (i) 信息丢失75%后的解密结果.
Fig. 9. Simulation results of anti-shear performance: (a) and (b) The sine- and cosine-holograms with 25% occlusion; (c) decryption result with 25% occlusion; (d) and (e) the sine- and cosine-holograms with 50% occlusion; (f) decryption result with 50% occlusion; (g) and (h) the sine- and cosine-holograms with 75% occlusion; (i) decryption result with 75% occlusion.
-
[1] Qin W, Peng X 2010 Opt. Lett. 35 118
 Google Scholar
Google Scholar
[2] Tsang P, Cheung K W K, Poon T C 2013 Chin. Opt. Lett. 11 27
[3] Unnikrishnan G, Joseph J, Singh K 2000 Opt. Lett. 25 887
 Google Scholar
Google Scholar
[4] Zhou N, Wang Y, He H, Gong L, Wu J 2011 Opt. Commun. 284 2789
 Google Scholar
Google Scholar
[5] Alfalou A, Brosseau C 2009 Adv. Opt. Photonics 1 589
 Google Scholar
Google Scholar
[6] Zhang Y, Wang B 2008 Opt. Lett. 33 2443
 Google Scholar
Google Scholar
[7] 姚丽莉, 袁操今, 强俊杰, 冯少彤, 聂守平 2016 65 214203
 Google Scholar
Google Scholar
Yao L L, Yuan C J, Qiang J J, Feng S T, Nie S P 2016 Acta Phys. Sin 65 214203
 Google Scholar
Google Scholar
[8] Refregier P, Javidi B 1995 Opt. Lett. 20 67
 Google Scholar
Google Scholar
[9] Takai N, Mifune Y 2002 Appl. Opt. 41 865
 Google Scholar
Google Scholar
[10] Matoba O, Javidi B 2004 Appl. Opt. 43 2915
 Google Scholar
Google Scholar
[11] Wu J H, Luo X Z, Zhou N R 2013 Opt. Laser Technol. 45 571
 Google Scholar
Google Scholar
[12] He M Z, Cai L Z, Liu Q, Wang X C, Meng X F 2005 Opt. Commun. 247 29
 Google Scholar
Google Scholar
[13] Situ G, Zhang J 2005 Opt. Lett. 30 1306
 Google Scholar
Google Scholar
[14] Qin Y, Gong Q 2013 Appl. Opt. 52 3987
 Google Scholar
Google Scholar
[15] Tajahuerce E, Matoba O, Verrall S C, Javidi B 2000 Appl. Opt. 39 2313
 Google Scholar
Google Scholar
[16] Carnicer A, Montes-Usategui M, Arcos S, Juvells I 2005 Opt. Lett. 30 1644
 Google Scholar
Google Scholar
[17] Peng X, Zhang P, Wei H, Yu B 2006 Opt. Lett. 31 1044
 Google Scholar
Google Scholar
[18] Poon T C, Korpel A 1979 Opt. Lett. 4 317
 Google Scholar
Google Scholar
[19] Poon T C 2009 J. Opt. Soc. Korea 13 406
 Google Scholar
Google Scholar
[20] Poon T C 2007 Optical Scanning Holography with MATLAB (Verlag: Springer) pp66−92
[21] Poon T C 1985 J. Opt. Soc. Am. A 2 521
 Google Scholar
Google Scholar
[22] Pan Y J, Jia W, Yu J J, Dobson K, Zhou C H, Wang Y T, Poon T C 2014 Opt. Lett 39 4176
 Google Scholar
Google Scholar
[23] Poon T C, Kim T, Doh K 2003 Appl. Opt 42 6496
 Google Scholar
Google Scholar
[24] Zhou X, Dobson K, Shinoda Y, Poon T C 2010 Opt. Lett 35 2934
 Google Scholar
Google Scholar
[25] 王仁德, 张亚萍, 王帆, 祝旭锋, 李重光, 张永安, 许蔚 2019 中国激光 46 0109001
Wang R D, Zhang Y P, Wang F, Zhu X F, Li C G, Zhang Y A, Xu W 2019 Chin. J. Laser 46 0109001
[26] Wang B, Zhang Y 2009 Opt. Commun. 282 3439
 Google Scholar
Google Scholar
[27] Chen W, Chen, X 2011 J. Opt. 13 115401
 Google Scholar
Google Scholar
计量
- 文章访问数: 12001
- PDF下载量: 114
- 被引次数: 0














 下载:
下载: